Aqua Security Surfaces Threat to Container Hosts
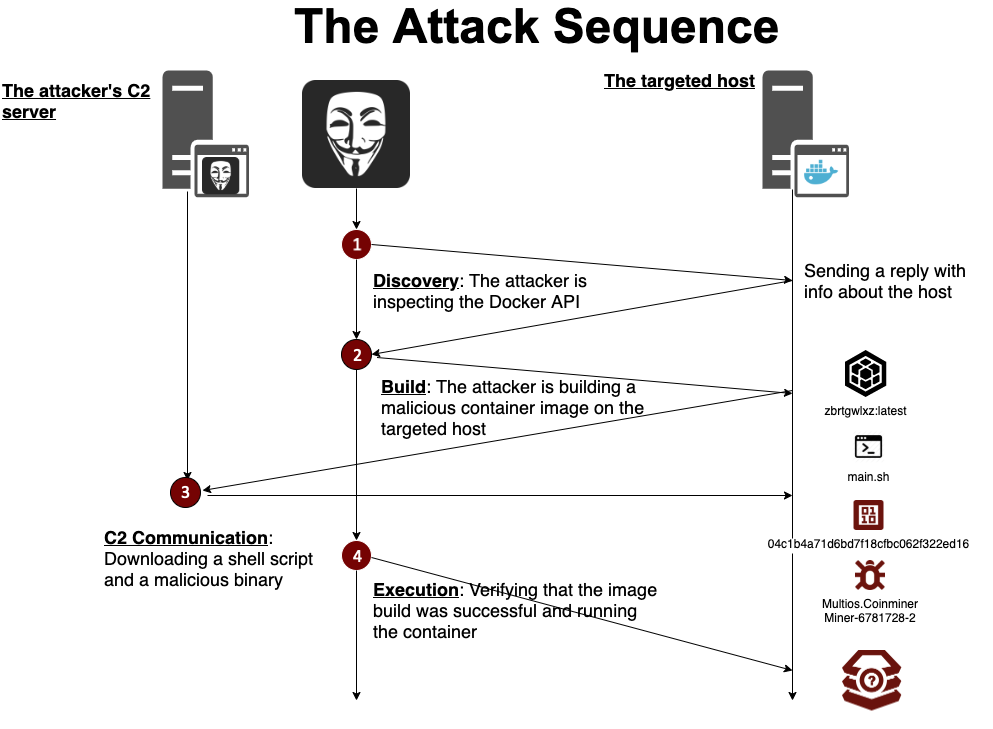
Aqua Security this week reported a new type of cyberattack that exploits Docker application programming interfaces (APIs) to build and run a malicious container image on the host.
Asaf Morag, lead data analyst for Aqua Security, says this approach enables cybercriminals to end-run static analysis tools that only discover malicious code prior to it being deployed in a runtime environment. Cybercriminals are essentially taking advantage of a host’s ability to spin up Docker containers in seconds to evade detection by static analysis tools, he says.
Previously, most container security research focused on container images before they are deployed. However, Morag notes it appears cybercriminals are now taking advantage of containers to launch attacks directly on the host.
Most of the attacks detected thus far have involved the surreptitious deployment of unwanted applications such as cryptomining software. IT teams should, however, assume this same attack vector is being employed to deploy more lethal forms of malware, says Morag.
Regardless of what type of malware may be deployed, Morag says it’s becoming increasingly clear IT teams need to scan container images before they are deployed and then continuously monitor deployment environments to make certain no container image is communicating with any service that has not been whitelisted.
In fact, Morag notes this attack makes it impossible to rely on blacklisting of hosts and container images because each new container spun up has a unique identifier.
In the grand scheme of cybersecurity, it’s not clear to what degree containerized applications are more secure than monolithic applications. It’s relatively simple to rip and replace containers that have known vulnerabilities. The challenge is the number of containers with the same vulnerable code can be staggering. There are also all the microservices dependent on that container to consider as well.
However, it’s much easier to replace a container than it is to patch a monolithic application. Many monolithic applications with known vulnerabilities might not be patched for a year or more. Containers make it possible to shift much of the responsibility for remediating vulnerabilities on to the shoulders of developers than build and manage them. Containers and microservice in many ways ultimately force IT organizations to adopt best DevSecOps processes.
There’s no doubt cybercriminals have determined how to exploit the same attributes of containers that make them so attractive to development teams. The challenge now is implementing a cybersecurity strategy that is comprehensive enough to thwart attacks all across the container life cycle. Otherwise, it’s just a matter of time before an exploit is employed to launch an attack that could compromise not just a single microservice but also all the microservices that have a dependency on it.
On the plus side, however, as more cybersecurity research is brought to bear on microservices and containers it’s probable the rate at which new issues arise and are addressed will accelerate. IT teams would be well-advised to not let those concerns distract them from containerized applications where the benefits continue to far outweigh any potential risk.