Aqua Security Reveals Sophisticated Container Attack
An alert concerning a container image that was deployed on a honeypot managed by Aqua Security suggests cybercriminals are getting a lot more sophisticated when it comes to scanning for container vulnerabilities.
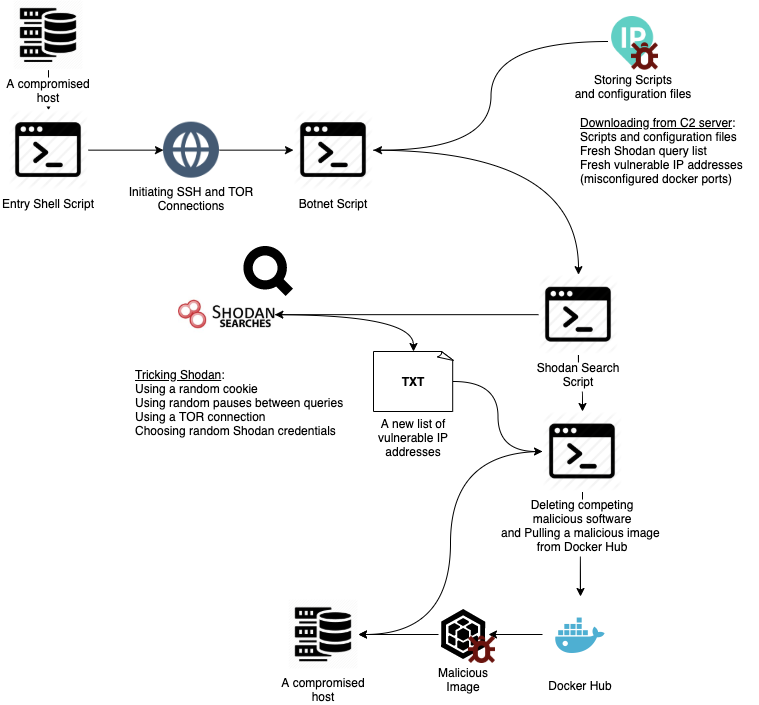
Aqua Security reports it has discovered a malicious container image that encapsulated a text file with a list of ~6K IPS hosts in one of its image layers. An analysis of the image revealed how some hackers are compromising hosts to launch malicious containers.
After a host is compromised, a malicious image is pulled from Docker Hub and then container entry point commands are run. TOR and SSH services are initiated to disguise outgoing traffic and open a backdoor to the attacker. A shell script designed to download further scripts and configuration files from the attacker’s C2 server is then deployed. The configuration files contain lists of search queries for a Shodan query engine, with a list of vulnerable IP addresses.
Once the Shodan search is executed, scripts are employed to generate enough random activity to not be blocked by the Shodan engine. Each compromised host is attacked using two scripts—the first seizes all competing malicious software and the other executes a malicious container image.
Assaf Morag, lead data analyst at Aqua Security, says the attacks are aimed at vulnerable IP addresses with a misconfigured Docker API on port 2375. This port is used by the Docker REST application programming interface (API) for unencrypted communication. Aqua Security was able to analyze data from 8,558 distinct vulnerable IP addresses, he says.
Out of those distinct IP addresses, 97 appeared in two attacks and eight IPs appeared in three attacks. It is unreasonable to assume any organization would expose such a crucial port for months, so Aqua Security researchers excluded those 97 IP addresses on the assumption they were honeypots being operated by some entity other than Aqua Security. The attacks themselves primarily targeted hosts running in China, the U.S., South Korea, Singapore, Japan, Brazil, Australia, Russia and India.
The five top services were vulnerable IP addresses belonging to Amazon, Alibaba, Verizon Communications, Tencent and Chiannet Network.
This latest report from Aqua Security comes on the heels of the revelations concerning how container hosts might be potentially compromised in a way that would evade static analysis tools. The latest disclosure indicates that attack vector is being exploited by cybercriminals with considerable container expertise.
Morag says these types of attacks are proof points for the need for cloud security posture management tools along with tools that dynamically scan images. In addition, IT teams adhere to least privileged access guidelines and avoid root user and privileged modes.
In the meantime, the debate over container security will continue to rage. Containers certainly make it easier to rip and replace vulnerable code. The issue is there can be thousands of containers with ephemeral lifespans that no one knows for sure whether they were compromised at some point in time. It might take many IT organizations some time to adjust to that level of uncertainty.