Latest Update to Harbor Registry Adds OCI Support
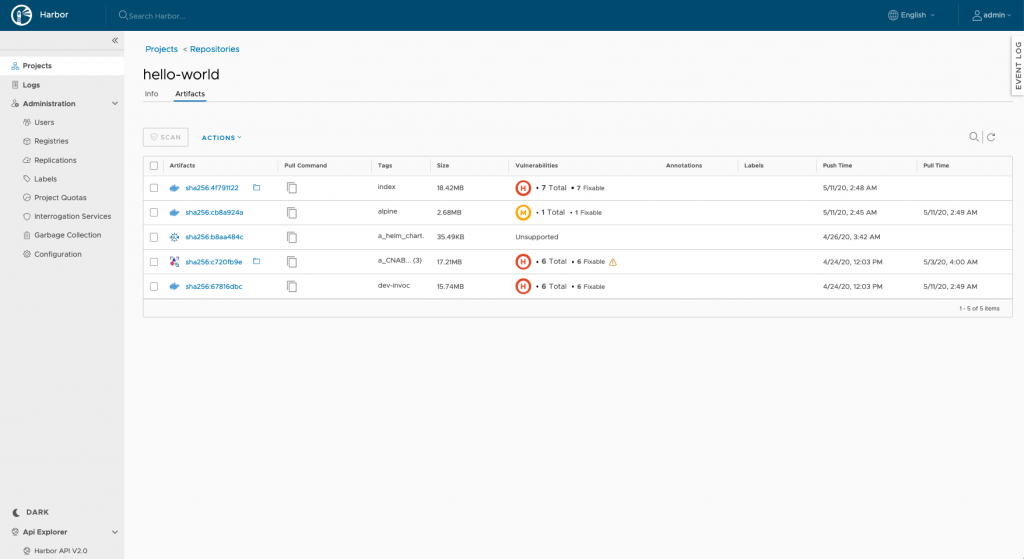
An update to the Harbor container registry that adds support for the Open Container Initiative (OCI) specification for Kubernetes clusters is now generally available.
Michael Michael, director of product management at VMware and a maintainer of Harbor, says OCI support also makes it possible to add other artifacts to the Harbor repository, such as Helm Charts. One of the attributes that distinguish Harbor—which was created by VMware and is now being developed under the auspices of the Cloud Native Computing Foundation (CNCF)—is that it can store artifacts other than containers in the same repository to help streamline DevOps workflows.
Harbor 2.0 also makes it possible to create an OCI Index, a higher-level manifest that provides a representation of a bundling of image manifests so users can pull an image without having to specify the operating system and platform. The client tool instead makes sure the correct version of an image is pulled.
With this release, Trivy replaces Clair as the default container image scanner. Trivy provides better performance and is simpler to invoke, Michael notes.
Harbor v2.0 also adds the ability to set an expiration date on each individual robot account. In a future release, robot accounts will be provided with the ability to be targeted to one or more projects, along with better credential handling for Kubernetes deployments.
Finally, Harbor v2.0 can now configure SSL to encrypt core Harbor services. Webhooks, which can be integrated with Slack for callbacks as an alternative to HTTP, also now can be individually triggered.
Michael says thus far there have been 60,000 downloads of Harbor, which is gaining traction as a registry because its ability to support multiple types of artifacts makes it easier to build applications by eliminating the need to manage multiple registries for each type of artifact.
In general, registries are emerging as the repositories around which developer workflows are being constructed. When many organizations first adopt containers, it is most often at a grassroots developer level. Before long, IT organizations discover multiple repositories have been created across the enterprise. Harbor presents an opportunity to bring some order to the building of containerized applications in a way that potentially fosters more reuse of container images.
In addition, repositories provide a central location to scan container images and other artifacts for vulnerabilities in a way that allows organizations to shift responsibility for security further left within the context of a set of best DevSecOps processes. Michael notes that registries are always a good first step toward implementing best DevSecOps practices, noting they can also play a key role in enforcing compliance mandates.
Harbor is still an incubating project within the CNCF, but support for the initiative continues to build alongside the adoption of Kubernetes. Michael says Harbor was developed specifically to address the requirements of enterprise IT organizations. It’s not clear just yet who within enterprise IT organizations will drive the standardization of container registries, but it should be more than apparent there is a pressing need to centralize the management of container images.