Canonical Allies With Docker Inc. on Secure Containers
Canonical has published a curated set of secure container application images on Docker Hub that it has committed to supporting for the next 10 years.
The company vowed to fix within 24 hours any critical security issues that impact any of the containers that become part of the Long Term Support (LTS) Docker Image Portfolio.
Company CEO Mark Shuttleworth says that commitment will enable organizations to apply best DevSecOps practices with confidence because the content within these containers will have been vetted by a vendor on their behalf.
Several of the images from the LTS Docker Image Portfolio will also be distributed as Docker Official Image versions during the five-year standard security maintenance period of the underlying Ubuntu LTS operating system.
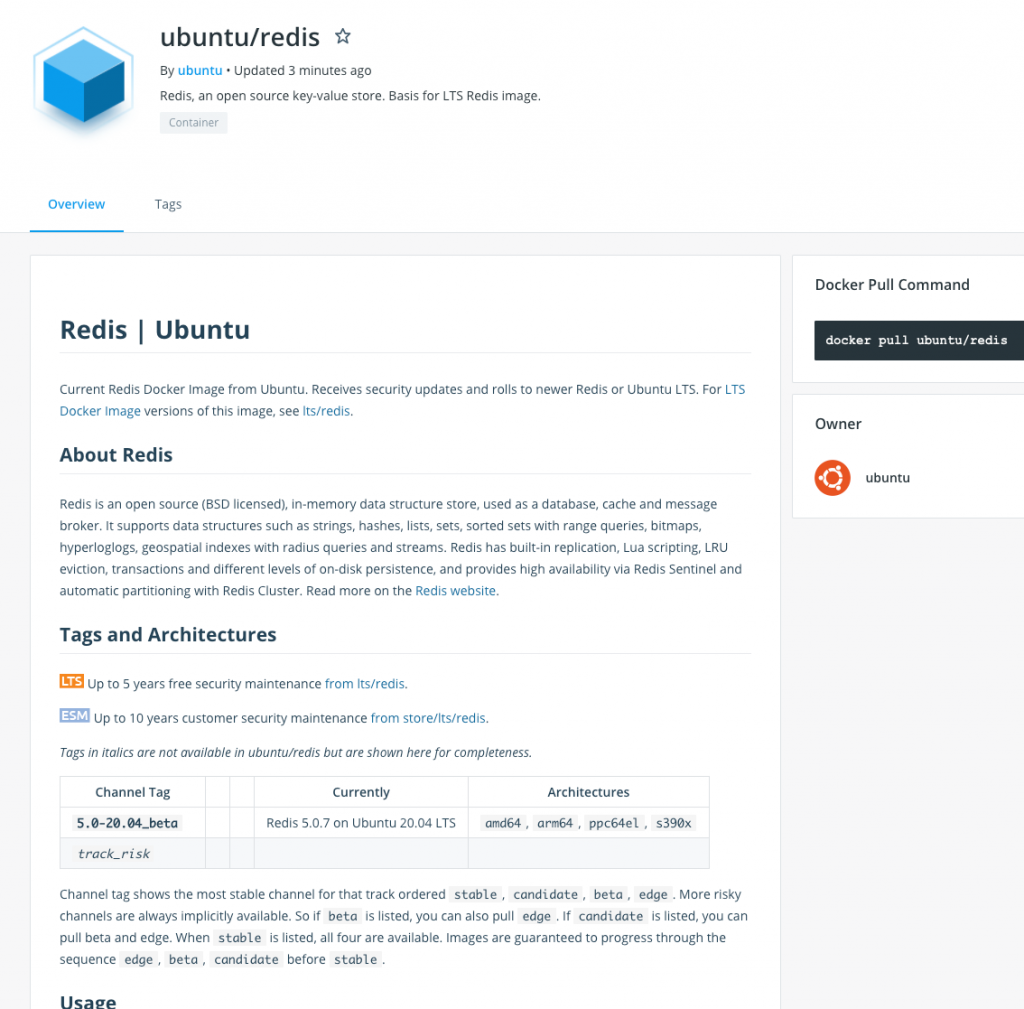
Company CEO Mark Shuttleworth says the LTS Docker Image Portfolio is part of an ongoing effort to extend the support services that Canonical provides well beyond the Ubuntu operating system. Images such as one for the open source Redis data store will also be exempted from per-user rate limits that Docker Inc. recently imposed.
 Docker Inc. CEO Scott Johnston says this alliance with Canonical extends a verified publisher initiative that already spans 200 organizations. There are now 160 Docker Official Images available via Docker Hub, which is accessed by more than 11 million active developers, according to the company. On average, Johnston notes there are more than 13+ billion pulls per month from 7.9 million application repositories that reside within the Docker Hub container registry.
Docker Inc. CEO Scott Johnston says this alliance with Canonical extends a verified publisher initiative that already spans 200 organizations. There are now 160 Docker Official Images available via Docker Hub, which is accessed by more than 11 million active developers, according to the company. On average, Johnston notes there are more than 13+ billion pulls per month from 7.9 million application repositories that reside within the Docker Hub container registry.
Docker Hub container registry is at the core of the ongoing effort to recast Docker Inc. as a provider of tools that optimize workflows for developers building container applications. Currently it is the largest public container registry employed; however, there are now several alternatives to Docker Hub that cloud service providers such as Amazon Web Services (AWS) are positioning as platforms that have no rate limitations. Those alternatives, however, will only make it more complicated for developers to employ container images across multiple platforms, notes Johnston.
In general, container security concerns are on the rise. Most of the instances involving malicious containers have involved cryptojacking efforts to mine digital currencies on cloud platforms. However, an innocuous-looking container on a public registry could be hiding a more lethal payload. Some containers might not contain that payload at all until they are downloaded; they then make an external call to download a piece of malware. The goal now is to make sure there are large numbers of verified container images available that IT organizations can employ knowing that the software included with the container is secure.
None of these security concerns appear to be slowing the rate at which container applications are being built and deployed. However, as the number of containers deployed in production environments continues to steadily increase, the potential for there to be a catastrophic security problem stemming from a container certainly starts to rise.




