Service Mesh Evolution: Ambient Mode, Gateways & The Return of Simpler Architectures
There was a time not long ago when implementing a service mesh felt like declaring a major infrastructure commitment. Sidecars injected into every pod, Envoy proxies humming alongside containers, control planes you had to monitor closely, configuration YAMLs deep enough to get lost in. But as with many things in the cloud-native world, complexity carries a cost — and adoption has shown this.
Now, service mesh is shifting. We’re entering a phase where the tools themselves are acknowledging user fatigue. Enter ambient mode, evolving Gateway APIs, lighter and layered architectures. What was once the domain of large, adventurous engineering orgs is becoming more accessible. We’re witnessing a return: Simpler, more flexible service mesh architectures that still deliver observability, security and traffic control — but without the full appetite sidecars demand.
What Sparked the Change
Red Hat’s announcement earlier in 2025 was a clear signal. In the blog “Red Hat advances OpenShift with ambient Service Mesh and scalable GitOps control plane”, Red Hat introduced ambient mode as a technology preview in OpenShift Service Mesh 3. Under that model, “the sidecar-overhead is not acceptable for particular applications,” so “this new mode eliminates the need for sidecar proxies by decoupling networking logic from application pods.”
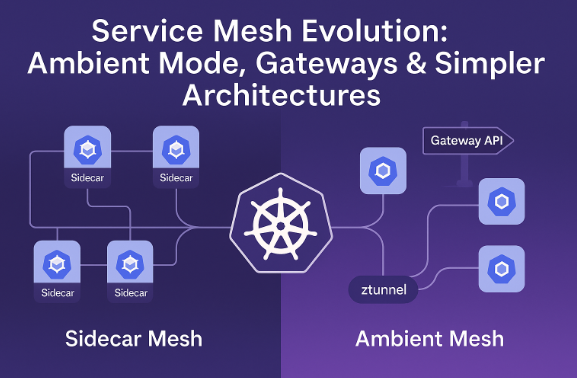
Instead of per-pod sidecars, OpenShift now supports a “node-level proxy” called ztunnel, plus optional Waypoint proxies in application namespaces for Layer-7 features like advanced routing or authorization.
Meanwhile, upstream in Istio’s ecosystem, ambient mode has matured. From the Istio blog: “service mesh without sidecars” is no longer just an experiment — it’s officially available in general availability as of Istio v1.24, including ztunnel, waypoints and stable APIs.
These changes did not come overnight. Feedback from many users has been consistent: Sidecars bring great capability, but for many applications, the operational and resource overhead is hard to justify. The ambient model promises something different—security, observability, traffic management — but with fewer moving parts.
What Ambient Mode & Gateway APIs Bring
Ambient mode isn’t just a fancy term. It introduces a two-layer data plane: A lightweight L4 overlay (node-level proxy like ztunnel) handling mTLS, identity, and basic traffic, with optional L7 proxies (waypoints) for services that need richer features. You can enable L7 only where you need it.
This architecture reduces the resource footprint. It simplifies upgrades. It makes onboarding new services less painful. Red Hat’s ambient mode reduces the “sidecar tax” by letting applications be part of the mesh without the sidecar-in-every-pod overhead. Developers no longer need to modify their apps just to satisfy mesh requirements, and platform teams breathe easier.
Gateway APIs add to the shift. As of OpenShift 3.1 (which tracks upstream Istio 1.26), Kubernetes Gateway API support is increasing. In OpenShift, Gateway API CRDs are now included by default in platform version 4.19 and later. This means using Gateway API to manage ingress/egress and mesh routing without custom CRDs becomes easier.
The combination of ambient mode plus Gateway API means platform teams can adopt mesh capabilities more incrementally. You can start with a secure L4 overlay, add mTLS, apply policies and observe basic traffic. Then, only if needed, enable richer L7 features via waypoints. This layered approach allows tailoring the mesh to needs rather than forcing a one-size-fits-all model.
Trade-Offs & What You Still Need to Watch
Of course, no architectural shift comes without trade-offs. Ambient mode in the current tech-preview or even general availability does not (yet) replicate all sidecar mode functionality for every use case. Some features remain in beta or alpha. For example, multi-cluster support, certain telemetry capabilities and cross-namespace mesh interactions may still require sidecar mode.
Another concern is security boundaries. Sidecars injected per pod have very fine-grained control. Moving to node or overlay proxies centralizes some of that authority. It demands careful identity and privilege design. Moreover, during upgrades of elements like ztunnel, connectivity may be temporarily affected, especially for long-lived connections. Red Hat’s guidance includes techniques like node cordoning or blue/green node pools to mitigate risk.
Observability is also changing, but not always uniformly. Waypoints, when enabled, can restore many L7 metrics and traces; but some latency, visibility, or debugging tools may still lag behind what sidecar mode once offered. Teams should test carefully under production-like loads.
Why Simpler Architecture Wins
All this might sound like incremental tweaks. But in practice, simpler architecture often wins. It wins in adoption, in maintainability, in predictable behavior under load.
For example, for many applications — especially internal services or lightweight microservices — the full sidecar model with Envoy proxies is overkill. The ambient architecture allows including them in the mesh without coercing every pod. This means less overhead, less resource waste, and fewer moving pieces to break. It aligns with the lean, DevOps approach many platform and SRE teams prefer.
Gateway API’s stabilization means you no longer need to rely on older custom resources or proprietary extensions. This standardization lowers the barrier to entry. It means better interoperability and easier evolution of tools. It means you get ingress, traffic routing, policies under clearer, unified APIs. This reduces complexity for operators, lowers risk and improves long-term maintainability.
What This Means for Practitioners
If you are running or planning service mesh in your organization, here are things to consider:
- Evaluate whether you need full sidecar mode for every workload. Can ambient mode cover most cases, reserving sidecars or waypoints for what truly needs L7-rich policies?
- When using ambient mode, use Gateway API if supported by your platform (e.g. OCP 4.19+ in OpenShift). That ensures you can manage ingress, egress, and mesh traffic under stable, supported CRDs.
- Pay attention to upgrade paths. Ambient mode is newer. Features still catching up. Ensure your observability and policy tooling works under ambient mode and that you perform good testing.
- Use smaller, controlled rollouts. Maybe start ambient mode for internal services or low-risk namespaces, observe behavior, then expand.
- Be mindful of security: Node-level proxies like ztunnel must be configured carefully; identity, certificate rotation, least privilege all still apply.
Shimmy’s Take
For too long, service mesh felt like the answer looking for a question — powerful, yes, but heavy and sometimes cumbersome. The shift to ambient mode and Gateway APIs doesn’t mean giving up on capabilities; it means being smarter about them.
Ambient mode represents maturity. It says: We heard you. You asked for better resource efficiency, lower operational overhead, easier adoption. The community answered.
Gateway APIs standardizing parts of the mesh (ingress, traffic routing, policies) unlock a simpler, more maintainable model. You don’t have to adopt everything at once. You can choose what you need.
In the end, simpler architecture doesn’t mean weaker architecture. If you design intentionally, with clear boundaries and solid observability, ambient mode + Gateways can deliver almost everything sidecar mode does — without the burden.
Service mesh isn’t going away. It’s evolving. And for many organizations, this evolution will make meshes a lot more usable. This is the era when mesh stops being a project you dread installing, and becomes one you quietly depend on.