Securing Cloud-Native Data at Rest
Data is central to all cloud-native applications, and keeping that data safe and secure is a challenge all application owners struggle with.
When discussing securing the data you use with your cloud-native application, you need to consider two types of data. The two types of data are data at rest and data in transit.
Data at rest is data that is being stored within your application in some type of data store. That data store could be a database, such as MySQL or Postgres, or simply files in a file system. For cloud-native applications, this could be a cloud database, such as DynamoDB, or a cloud object store, such as Amazon S3.
A simple example of data at rest is your list of customers, their email addresses, their login credentials and other personal information about those customers. Data specific to the application is also included, such as order history information, product details and inventory levels for an e-commerce store.
Data in transit is data that is moving into and out of your application from either your customers or to external services and systems (data in transit externally). But it also refers to data moving from one service or location within your application to another service or location within your application (data in transit internally).
A simple example of data in transit is a login page where customers send you their login credentials to validate who they are. A money transfer request, a sent text message and an order request are all examples of data in transit. Even analytics data, such as application logs and performance data sent to an external partner for analysis, can be considered data in transit.
Figure 1 illustrates these data types in a simple application. Here, data is transmitted from the external user to an internal service, from an internal service to and from the database and between internal services are all examples of data in transit. Meanwhile, data stored in the database itself is data at rest.

The techniques you use for securely dealing with data differ between data in transit and data at rest.
Securing Data at Rest
Data at rest can be secured by encrypting the data before it is stored. If someone attempted to access the stored data, they would be unable to decrypt the data without the proper keys and would not be able to steal the data successfully.
A critical issue with encrypting stored data is where and how to store the decryption keys. You do not want to store them in the same location as the data itself, as that removes the security advantages of decryption. Storing your decryption keys in the same location as your encrypted data is much like putting your home’s front door key under your doormat. Your home is essentially unsecured. The same is true if your encrypted data is stored next to your encryption keys.
But where do you put your encryption keys so they are usable by your application when necessary but are not readily available to be stolen along with your data? There are many options—simple or complex—but one excellent option for a cloud application is to use a key storage service offered by your cloud provider. Many key storage services provide one or multiple levels of key storage to protect your credentials from being stolen.
Don’t Store Data at All
Sometimes, though, securing data at rest is best done by not storing the data at all. A classic example is credit card information. There is very little reason for nearly any website ever to store credit card information—encrypted or not—within the application. This applies to e-commerce stores as well as content subscription sites. Even sites that charge a customer’s credit card on a recurring basis do not need to store the credit card information within the application. Instead, use a credit card processing third party, such as Stripe, Square or PayPal. They manage the entire process of storing and processing the transactions and they give you a token that you hold on your site that refers to the credit card and scheduled transactions.
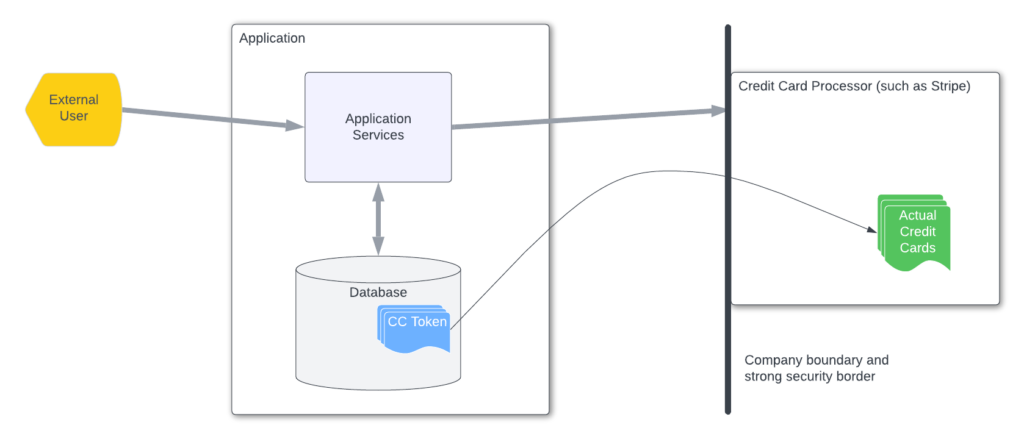
Figure 2 shows the use of these credit card tokens. This token allows you and your application to use the stored credit card information on the processor’s site without ever having access to the credit card details themselves. The large firewall between your application and the provider means that even if a bad actor gets your CC tokens, they can’t use them to get the full credit card details. These tokens are useless to a bad actor if your website is compromised because they can be readily disabled without impacting the customer or their credit card information.
Stored Data is Less Dynamic
An important thing to keep in mind with data at rest is the data tends to be less dynamic than data in transit—stored data doesn’t tend to change very often. This means that whatever mechanism you use to secure the data will likely be used for an extended period without disrupting application operations.
This means that simple security operations, such as rotating encryption keys, can be more difficult for data at rest. This is because you need to decrypt the data using the old keys before you re-encrypt the data using the new keys. This can involve re-encrypting potentially large amounts of data, and doing this simple key rotation can put your data at increased risk during the process.
This means you typically only rotate keys when you access and modify the data. If data isn’t touched for a significant period or is mostly read/only data, then the opportunity to rotate keys tends not to come up very often. This can increase the complexity of managing data since multiple encryption keys need to be juggled for similar data purposes.
Keeping Data Safe
Data at rest is straightforward, but keeping it safely encrypted for long periods can be daunting when facing security best practices such as key rotation. Data in transit is both easier and harder to deal with than data at rest. Cloud-native application security is critical for everybody, and keeping applications safe and secure is an important topic.
This article talked about protecting data at rest. Next week we will talk about securing data in transit.




