Fugue Adds Kubernetes Support to IaC Security Platform
Fugue today at the KubeCon + CloudNativeCon North America conference announced that its software-as-a-service (SaaS) platform for securing infrastructure-as-a-code (IaC) deployments now also supports Kubernetes clusters.
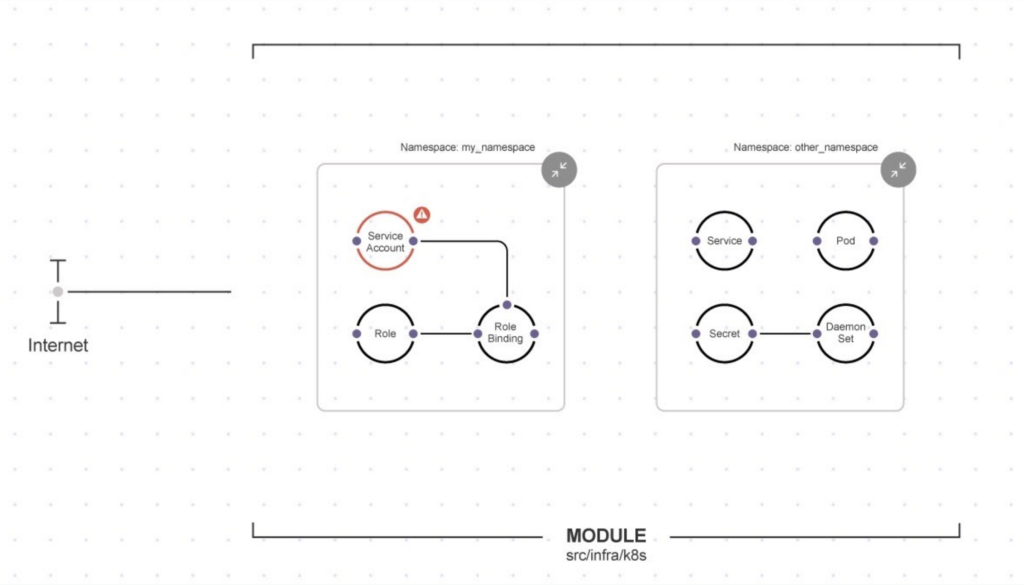
Josh Stella, Fugue CEO, says that as developers increasingly take it upon themselves to programmatically deploy Kubernetes clusters the chances are high that one of the most complex IT platforms ever created will be misconfigured.
The Fugue platform employs policy-as-code automation, based on the open source Regula policy engine, to ensure the proper controls are implemented using, for example, rules that align with the Kubernetes Benchmark created by the Center for Internet Security (CIS), adds Stella. Regula is a declarative programming language that employs the Open Policy Agent (OPA) software being developed under the auspices of the Cloud Native Computing Foundation (CNCF) to enforce policies.
The Fugue SaaS platform and Regula project include hundreds of pre-built policies mapped to the CIS Foundation benchmarks for Amazon Web Services (AWS), Microsoft Azure, Google Cloud and Kubernetes. It also provides compliance mapping for SOC 2, NIST 800-53, GDPR, PCI, HIPAA, ISO 27001, CSA CCM, CIS Controls, CIS Docker and the Fugue Best Practices Framework to identify misconfigurations that might not otherwise be discovered.
Collectively, the Fugue platform makes it simpler to consistently implement policies and controls across a diverse range of infrastructure platforms, notes Stella.
In general, Stella says that while there is a learning curve for developers that are implementing policy-as-code using Regula, the language itself isn’t all the different than SQL in terms of its overall complexity. As such, Regula and OPA are quickly emerging as a de facto standard for implementing policy-as-code in cloud-native application environments within the context of a DevOps workflow, says Stella.
Fugue last month extended its platform for securing IaC deployment to now also include the runtime environments upon which applications are deployed. The company claims that extension can reduce the engineering resources required to secure an IT environment by 50% or more because a separate platform is no longer required to secure the infrastructure on which applications are deployed.
Interest in tools like Fugue is on the rise because IT organizations are discovering that the cloud platforms that they deploy applications on today are often rife with misconfigurations. Developers often use tools like Terraform to provision infrastructure themselves with no guidance from IT operations or security teams. The issue is that most of those developers have little to no security expertise, so there’s a better-than-good chance mistakes will be made.
Despite those security concerns, however, organizations are reluctant to slow down the rate at which applications are being built and deployed. The Fugue platform essentially gives IT teams a platform with a self-healing capability that can be easily implemented, says Stella,
It may be a while before DevSecOps best practices include tools for securing IaC deployments. However, given the prevalence of the issue, it may now be a matter of when versus if that will occur.