Fairwinds Automates Remediation of Kubernetes Misconfigurations
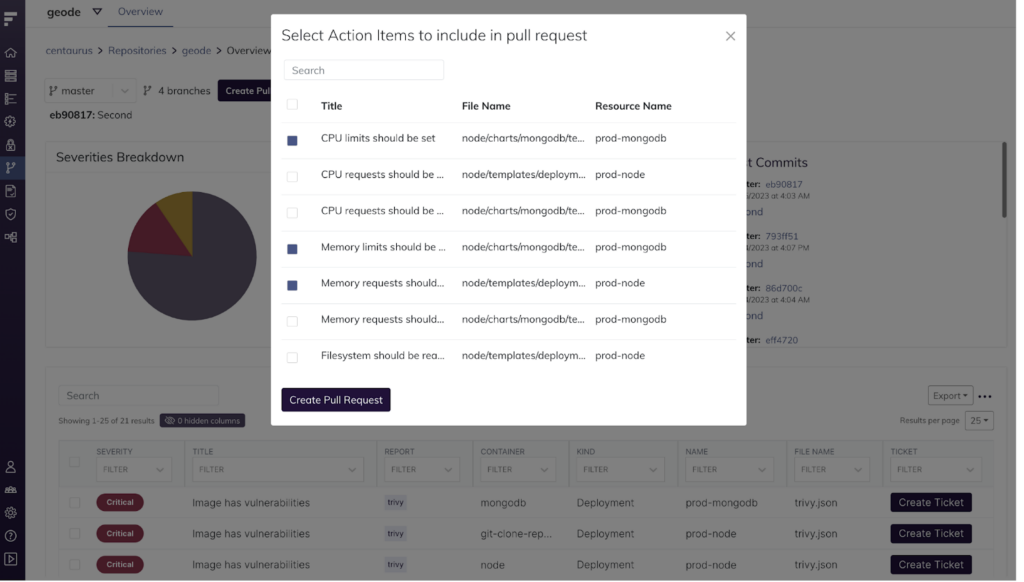
Fairwinds this week added an Automated Fix Pull Requests (PRs) capability to its commercial platforms that identifies and automatically remediates Kubernetes misconfigurations.
Joe Pelletier, vice president of product at Fairwinds, says this addition to the Fairwinds Insights Kubernetes management platform extends an existing capability to scan infrastructure-as-code (IaC) created using tools such as Terraform.
Automated Fix PRs creates an automated feedback loop by identifying issues and then surfacing recommended fixes. The platform can then automatically apply those fixes to a GitHub repository. At present, about 40% of the fixes surfaced can be automatically applied, a percentage that will steadily increase as additional updates to Automated Fix PRs are made.
The goal is to increase developers’ productivity by reducing the amount of time it takes to find and remediate an issue. The goal is to make sure these tasks can be accomplished in a matter of minutes, says Pelletier. That approach makes it more likely developers will address these issues versus continuing to opt to focus their efforts on writing more application code, he adds.
These automated remediation capabilities can already be found in Fairwinds Polaris, an open source policy engine that Fairwinds makes available. Fairwinds Insights provides a commercially supported instance of that capability that more tightly integrates with GitHub; support for other repositories is being considered, says Pelletier.
In general, in the age of infrastructure-as-code (IaC) tools, misconfigurations are a major thorn in IT’s side. Developers that have little to no infrastructure or security experience are provisioning infrastructure, so the odds mistakes will be made are fairly high. The challenge is making it as simple as possible for developers to remediate these issues without requiring them to write a lot of code.
Of course, that issue is especially problematic in Kubernetes environments. Arguably, Kubernetes is both the most powerful and complex platform to find its way into production environments in recent times. As such, it’s even more probable that a Kubernetes cluster will be misconfigured.
Ultimately, the simpler it becomes to manage and secure Kubernetes clusters, the more adoption there will be. Many IT teams are still intimidated by the platform that was designed for engineers by engineers; not surprisingly, traditional IT teams are encountering multiple issues. A recent Fairwinds analysis of more than 150,000 workloads running in Kubernetes clusters deployed by hundreds of different organizations finds organizations are not following best practices for managing cloud-native application environments.
For example, 30% of organizations have at least 50% of their workloads set with memory limits that are too high. A full 83% of organizations are not setting liveness or readiness probes for more than 10% of Kubernetes workloads. The report finds organizations that implemented Kubernetes guardrails were able to correct 36% more issues where CPU and memory configurations were missing than those that did not have guardrails in place. IT teams leveraging guardrails were also able to repair 15% more image vulnerabilities than those not using them.
One way or another, the management of Kubernetes is going to get easier; the only thing to be determined now is how much pain will be experienced between now and then.