Deepfence Expands Scope of Open Source Container Security Platform
Deepfence today announced it has updated its open source ThreatMapper project to add expanded visualizations of attack paths and a scanner based on the YARA tool many security researchers use to identify and classify malware samples.
In addition, version 4.1 of ThreatMapper now includes enterprise-grade cloud security posture management (CSPM) tools to make it simpler to meet compliance mandates.
Deepfence CEO Sandeep Lahane says as the economy continues to stagnate, the rate at which organizations are embracing open source cybersecurity tools is only going to accelerate. In fact, as the economy falters, attacks are only increasing in volume and sophistication, which Lahane predicts will create a perfect storm for application security.
ThreatMapper has evolved into an open cloud-native application protection platform (CNAPP) for scanning, mapping and ranking vulnerabilities in running pods, images, hosts and repositories, says Lahane. It scans for known and unknown vulnerabilities, secrets and cloud misconfigurations at runtime or within a continuous integration/continuous delivery (CI/CD) platform and then puts those findings in context using graph technology to improve DevSecOps workflows.
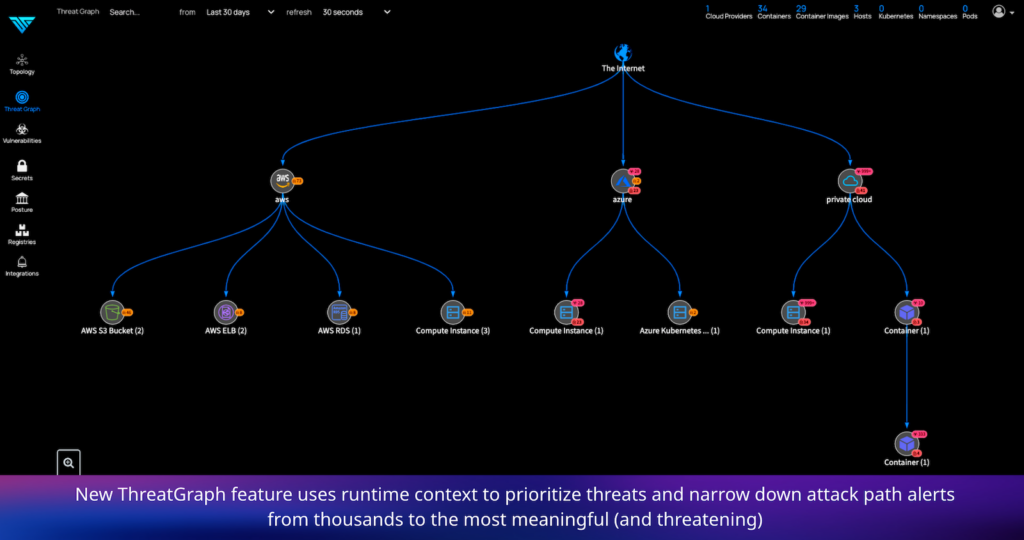
That ThreatGraph capability in the latest release of ThreatMapper has been expanded to include network flows to better prioritize threat scan results as part of an effort to identify the most critical attack path alerts.
Deepfence has also integrated a variety of agentless compliance controls that are now mapped to cloud assets to make it simpler to improve overall security posture.
ThreatGraph also makes it easier for IT organizations to construct a software bill of materials (SBOM) by surfacing all the relationships between the components of an application, notes Lahane.
In general, CNAPP offerings such as ThreatMapper are making it easier for cybersecurity teams working in collaboration with DevOps teams to consolidate a wide range of cybersecurity processes that previously would have required multiple point products. The issue those teams encounter when employing those point products is that they each require staff to deploy and maintain. A CNAPP affords organizations the ability to invoke a range of security functions without necessarily having to increase staff at a time when cybersecurity expertise continues to be hard to find and retain, notes Lahane.
It’s not clear to what degree the rise of modern application environments based on microservices constructed using containers will force the DevSecOps adoption issue. However, it’s apparent that securing highly dynamic application environments is not going to occur without relying more on some form of automation. Developers and DevOps teams generally lack the expertise required to secure applications, and there are simply not enough security professionals available to secure these environments. The issue then becomes finding cybersecurity platforms that integrate well into application development workflows that can be adopted at a reasonable cost.
In many cases, organizations that don’t have a lot of financial resources to allocate to application security will naturally embrace open source tools that are both readily available and don’t require the approval of a purchasing manager to use. Not every cybersecurity professional, of course, may approve of the selection process, but at the end of the day, the goal is to determine how to ensure security in the least disruptive way possible.