Contrast Security Integrates AppSec Platform With OpenShift
Contrast Security has integrated its vulnerability scanning and runtime application self-protection (RASP) portfolio with the Red Hat OpenShift platform for building cloud-native applications.
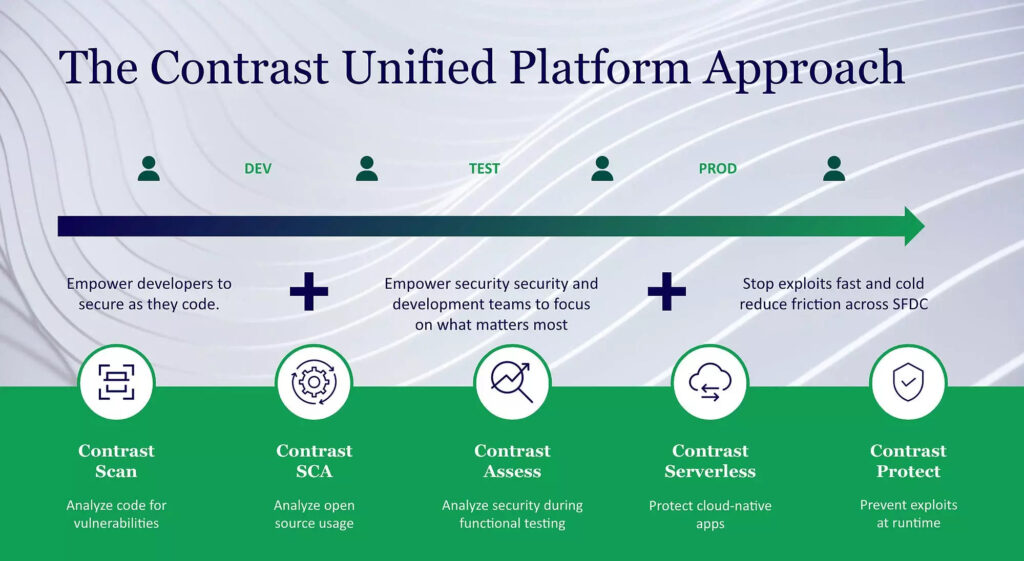
Jeff Williams, Contrast Security CTO, says this integration makes it possible to deploy the Contrast Secure Coding Platform application security framework as a set of containers that can be deployed within an application development and deployment platform based on Kubernetes.
A set of application programming interfaces (APIs) make it possible to automatically scan code at build time in addition to making use of a RASP platform to secure cloud-native applications at runtime by adding agent software to their applications, he notes. That makes it possible to automate security processes within a set of repeatable pipeline templates, adds Williams.
Contrast Security has been making a case for employing its platform as the foundation for implementing DevSecOps best practices to build monolithic applications. That capability is now being extended to include microservices-based applications constructed using containers.
In general, Williams notes there is too much emphasis on shifting responsibility for application security toward developers. While providing developers with the tools and skills required to build secure applications is desirable, Williams adds that developers, like most humans, will make mistakes. The only way to truly ensure application security is to integrate both static and dynamic application security testing tools with a RASP platform that is tightly integrated within a DevOps workflow.
DevSecOps as a discipline is still in the early stages of adoption. The overarching goal is to create a secure software development process by eliminating silos and encouraging collaboration between developers and security teams. By inserting security audits and penetration testing into the development process, for example, organizations can improve the security of applications before they are deployed in a production environment. That approach allows DevOps teams to remediate most issues before they are already deployed in a production environment and become much more expensive to fix.
As valid as that goal may seem, it requires first giving developers and DevOps teams the tools to build and deploy more secure applications and then bridge the historic divide that has existed between development and cybersecurity teams. That latter part is crucial because the policies that DevOps teams are typically implementing are defined by the same cybersecurity teams that are later determining whether an application is secure enough to deploy. Unfortunately, most application development teams have experienced an application get pulled back from deployment at the last minute because of the discovery of an unexpected security issue.
Microservices-based applications, of course, only further complicate that challenge. This is because of all the dependencies that exist between the components of loosely coupled application components connected via an application programming interface (API). Each of those components is frequently updated, so the opportunity to accidentally introduce additional vulnerabilities is high. Organizations also need to secure the APIs that have been created to connect each microservice.
Ultimately, organizations will soon be routinely deploying secure applications. That journey, however, is only just beginning.