Deploy Serverless Lambdas Confidently with Canary
In today’s fast-paced software development environment, continuous deployment (CD) is essential for delivering frequent updates without disrupting production. AWS Lambda, being serverless, requires careful deployment strategies to ensure seamless updates while minimizing risk. One of the most effective methods is canary deployments, which allows for gradual rollouts with built-in monitoring and rollback mechanisms.
This article explores Lambda function releases using CD pipelines and canary deployments, comparing deployment strategies, detailing best practices and offering insights on making releases safer and faster.
Deployment Strategies
Choosing the right deployment strategy is crucial for balancing speed, stability and risk management. Here are two primary strategies:
Rolling Deployment
A rolling deployment updates function instances incrementally, replacing old versions in batches. This ensures zero downtime, but different users may experience different versions during the transition.
Pros:
- No service downtime
- Simple to implement
- Lower infrastructure costs
Cons:
- Potential version inconsistency
- Rollback can take longer
Canary Deployment
In a canary deployment, traffic is split between the old and new versions of the function, initially sending a small percentage to the new version. If no issues arise, the deployment progresses until all traffic is shifted.
Pros:
- Limits blast radius of failures
- Allows real-world performance monitoring
- Instant rollback
Cons:
- Slightly more complex setup
- Requires traffic routing control
For AWS Lambda, canary deployments provide the best balance of risk and agility, especially when paired with automated monitoring and rollback mechanisms.
Canary Deployment in AWS Lambda
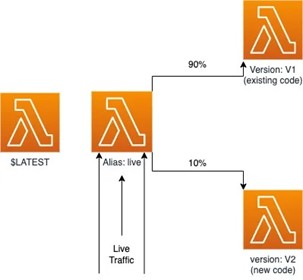
AWS Lambda supports versioning and alias-based deployments to manage traffic shifting safely.
Versions and Aliases
- Versioning: Each Lambda function version is immutable, enabling easy rollbacks.
- Aliases: Named pointers (e.g., prod) route traffic to a specific version and support weighted traffic distribution for canary rollouts.
Best practice: Always bind event sources (e.g., API Gateway, S3, EventBridge) to the alias,
not the $LATEST version.
Traffic Shifting with AWS CodeDeploy
AWS CodeDeploy simplifies canary rollouts by shifting traffic automatically or manually based on predefined deployment strategies:
- Time-Based Canary: AWS shifts 10% traffic for a set time (e.g., five minutes), then promotes the new version if no issues occur.
- Approval-Based Canary: Requires manual approval before full rollout, giving teams control over production releases.
With AWS CodeDeploy, CloudWatch Alarms can trigger automatic rollbacks if failures or latency spikes occur.
Best Practices for Safe Lambda Deployments
1. Use CI/CD for Automated Deployment
Set up a CI/CD pipeline using AWS CodePipeline or third-party tools (e.g., GitHub Actions, Jenkins) to automate builds, tests and deployments.
2. Start with a Small Canary
Deploy 5–10% of traffic to the new version, increasing gradually. This ensures that if a problem exists, only a small portion of users are affected.
3. Monitor Key Metrics During Deployment
Use Amazon CloudWatch to track:
- Errors (e.g., invocation failures, timeouts)
- Duration (execution time changes)
- Concurrency & Throttling (provisioned vs. on-demand usage)
4. Configure Automated Rollbacks
Set CloudWatch alarms for key metrics and configure AWS CodeDeploy to automatically roll back the deployment if an anomaly is detected.
5. Use Manual Approvals for Critical Deployments
For high-risk deployments, insert a manual approval step in AWS CodePipeline to allow engineers to verify logs and metrics before full rollout.
6. Route All Event Triggers to an Alias
Ensure all event sources (API Gateway, S3, EventBridge) invoke the alias (prod) instead of a specific function version to enable smooth traffic shifting.
7. Test Rollbacks in a Staging Environment
Before production deployments, intentionally fail a deployment in a staging setup to verify that the rollback mechanism functions correctly.
8. Avoid Hard Dependencies in Rollbacks
Ensure database schema updates are backward-compatible, and do not make irreversible changes during a canary release.
9. Use AWS SAM or CDK for Deployment Automation
AWS Serverless Application Model (SAM) and AWS Cloud Development Kit (CDK) simplify canary deployments by defining deployment preferences in infrastructure as code.
10. Enable Logging & Tracing for Debugging
Use AWS X-Ray for tracing function performance across different versions. Ensure CloudWatch Logs capture errors to diagnose failed deployments quickly.
Common Pitfalls and How to Avoid Them
❌ Forgetting to Attach Triggers to the Alias
If an event source invokes $LATEST instead of an alias, 100% traffic could go to the latest version unexpectedly.
✔ Solution: Always configure event sources to invoke the alias, not $LATEST.
❌ Not Setting Up CloudWatch Alarms
Deploying without alarms means CodeDeploy won’t detect issues, leading to faulty releases affecting all users.
✔ Solution: Set alarms for error rates and latency to trigger automatic rollbacks.
❌ Low-Traffic Environments May See Unbalanced Canary Distribution
With low request volumes, a 10% canary may not accurately distribute traffic, causing some users to get 100% of the latest version.
✔ Solution: In low-traffic services, use approval-based deployments instead of automated canaries.
❌ Provisioned Concurrency Mismanagement
If provisioned concurrency is enabled, canary deployments may not allocate enough instances, leading to cold starts for some requests.
✔ Solution: Scale both old and new versions appropriately to ensure smooth transitions.
Final Thoughts
Adopting continuous deployment with canary releases in AWS Lambda allows for frequent, risk-free deployments. By leveraging AWS CodeDeploy, CloudWatch monitoring, and alias-based traffic shifting, teams can roll out new versions confidently while maintaining high reliability.