Portshift Ties Cybersecurity Policies to Container Vulnerabilities
Portshift announced it has extended a platform that enables organizations to create a zero-trust application environment by assigning identities to microservices, which then allows them to apply policies to restrict access to containers with known vulnerabilities until a developer can replace those containers.
Zohar Kaufman, vice president of research and development for Portshift, says the company’s namesake platform has been extended to identify vulnerabilities in containers by integrating with container scanning tools such as Clair, an open source tool developed by CoreOS. Portshift plans to add support for other container security tools from Twistlock and Aqua Security, he says.
The Portshift platform attaches identities to applications and services as they are being built on a continuous integration/continuous delivery (CI/CD) platform to enable IT teams to create a zero-trust IT environment. A Policy Advisor recently added by Portshift extends that capability to microservices by installing agent software on a Kubernetes cluster.
By integrating with container scanning tools, Policy Advisor can now better inform IT teams of what communication links between microservices should be blocked, in addition to determining which policies should be enforced at runtime based on the vulnerabilities identified in any given set of containers, says Kaufman.
That approach also enables IT teams to assess the severity of those vulnerabilities. Some may opt to not replace a container immediately if the severity of the vulnerability is not that high. In effect, Portshift enables IT teams to better prioritize their efforts to remediate container vulnerabilities, says Kaufman.
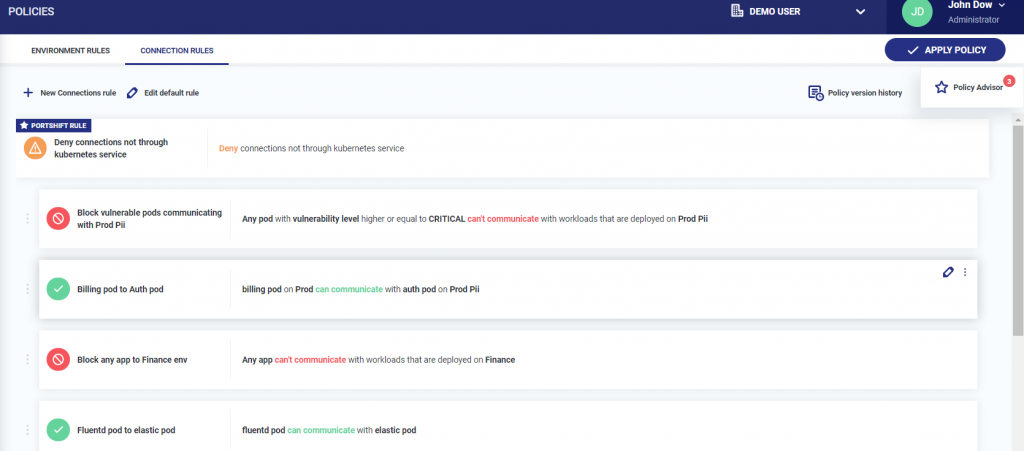
Portshift also provides an easier way to secure microservices that goes beyond trying to rely on firewalls that don’t dynamically adjust to changes to the application environment. Policy Advisor gives IT teams the option to create rules based on suggestions surfaced by the platform or create custom rules to meet specific runtime requirements.
Administrators can select a suggested rule from a policies page that shows the source, destination, traffic details and pending actions. The Policy Advisor then identifies the number of connections that could be affected by the rule to prevent what otherwise might be an unintended consequence. Once executed, the new rule will appear in the connection policy window, which the administrator then can save, modify or delete.
Kaufman says IT organizations should expect to see the company integrate its platform with a range of DevOps tools via an open application programming interface (API) it has created. The goal is to make it possible to attach identity to any service, which in turn makes it easier to manage microservices at a higher level via the visualization tools provided by the Portshift platform, he notes.
As the number of microservices within an IT environment continues to multiply, IT teams will need to find a way to manage and secure them at higher levels of abstraction. Recent surveys suggest usage of microservices is already widespread. The challenge now is not only finding ways to build, deploy and manage microservices at scale but also to make sure the connections between those microservices are secure.