Aqua Security Extends Container Security Platform
Aqua Security today launched a tool today that dynamically scans container environments to discover more sophisticated forms of malware that often elude static analysis tools.
Rani Osnat, vice president of strategy for Aqua Security, says Aqua Dynamic Threat Analysis (DTA) will be available as both a standalone tool and as an option of the Aqua Cloud Native Security Platform, a software-as-a-service (SaaS) offering that the company added last year by acquiring CloudSploit.
Aqua Security also has also revamped the cloud security posture management (CSPM) solution it gained via the acquisition. Rechristened Aqua CSPM, the offering now includes a preview version of both Aqua DTA and a container image vulnerability scanning based on the open source Trivy project created by the company. The vulnerability scanner currently supports Amazon Web Services (AWS) environments, with additional registry support planned throughout the year. Aqua CSPM is the only integrated platform that discovers container image registries, scans images for vulnerabilities and detects hidden malware threats within a seamless workflow, says Osnat.
Other enhancements to Aqua CSPM include general availability for support for Google Cloud and Oracle Cloud environments, the ability to scan Terraform templates alongside previous support for AWS CloudFormation templates and the ability to automatically General Data Protection Rule (GDPR) reports.
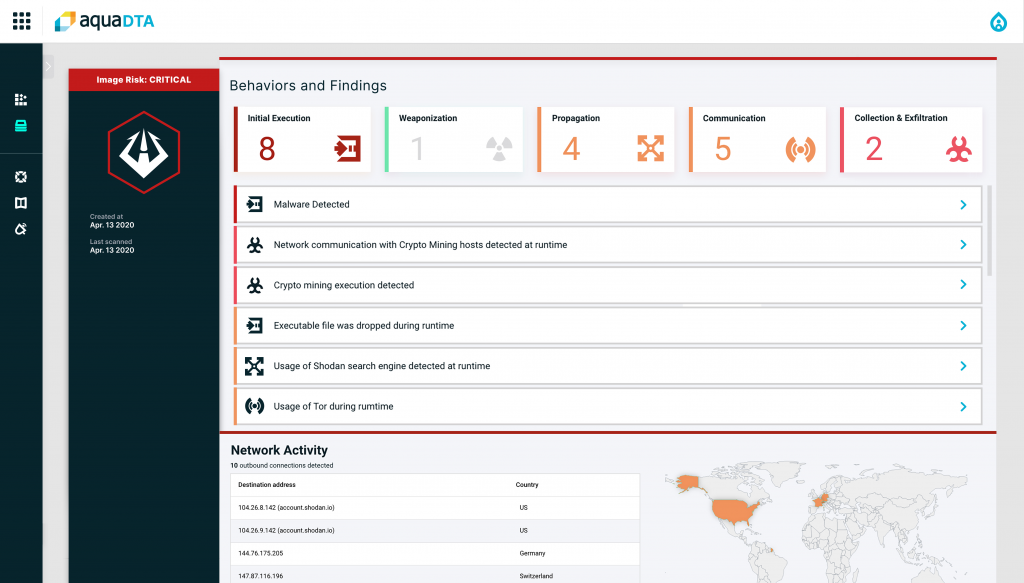
Osnat says that as cybercriminals increasingly target containers and Docker application programming interfaces (APIs), there are more zero-day threats being incorporated into containers that developers inadvertently reuse. Those threats manifest themselves in container images that contain encrypted polymorphic malware that changes behavior to escape detection by, for example, unpacking malicious payloads during runtime, opening a reverse shell or executing malware from memory.
The Aqua DTA creates a sandbox that runs those images to discover the precise nature of a zero-day threat, says Osnat. That sandbox can be configured to automatically scan only images within a specific scope based on, for example, a label or within a specific named registry. Static scanning tools are not designed to discover sophisticated polymorphic threats, he notes.
In general, Osnat says maintaining container cybersecurity becomes more challenging as the number of pods being run within a Kubernetes cluster increases. As the number of pods increases, it becomes increasingly apparent there is a need to automate malware detection workflows within the context of a set of best DevSecOps processes, he says.
Of course, it’s not clear to what degree the adoption of containers winds up forcing the DevSecOps issue within organizations. Most organizations are still in the early stages of adopting DevSecOps. However, as the IT environment becomes more complex there is a much stronger need to implement cybersecurity controls at the earliest stage of the application development process.
The challenge is that as more developers reuse container images to build applications, the greater the opportunity becomes for cybercriminals to compromise the integrity of those images. As a result, the level of scrutiny that needs to be applied to every container image employed is now reaching a point automating the scanning process is now nothing less than a prerequisite.