Aviatrix Adds Kubernetes Firewall to Secure Cloud-Native Platforms
Aviatrix has launched a Kubernetes firewall designed to specifically address the unique requirements of cloud-native computing environments that typically consume ten times as many IP addresses than legacy platforms.
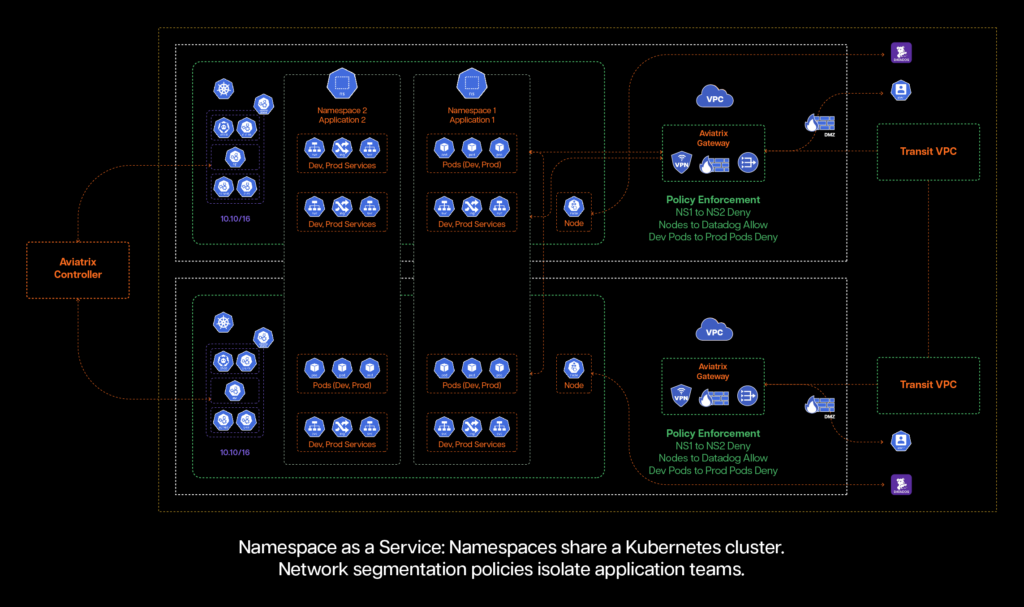
Company CTO Anirban Sengupta said the Aviatrix Kubernetes Firewall dynamically enforces cybersecurity policies based on the namespace identity of the cluster rather than the IP addresses being used.
That’s critical because Kubernetes clusters rapidly exhaust the number of IP addresses available, resulting in overlapping classless inter-domain routing (CIDR) blocks spanning multiple clusters that cause connectivity failures. The Aviatrix Kubernetes Firewall takes advantage of built-in network address translation (NAT) capabilities to eliminate that dependency in a way that ensures cybersecurity policies are enforced as any workaround for the lack of IP addresses available might need to be implemented, said Sengupta.
Of course, the lack of available addresses is more critical for organizations that are dependent on IP-4 versus IP-6, but regardless of which version of the protocol is used, basing cybersecurity policy enforcement based on the identity of a cluster provides IT organizations with more granular control that enables them to more consistently meet compliance mandates, added Sengupta.
That issue is becoming more pressing because Kubernetes clusters typically run high-value applications workloads, including artificial intelligence (AI) models and agents, that are tempting targets for cybercriminals, he noted.
The Aviatrix Kubernetes Firewall is based on the same core engine that Aviatrix originally developed for the Aviatrix Cloud Firewall. As the number of Kubernetes clusters being deployed in production environments continues to steadily increase, it’s become apparent that those same capabilities need to be applied directly to hybrid computing environments running multiple types of Kubernetes clusters, said Sengupta.
That approach also enables organizations to centrally apply the same cybersecurity policies to both monolithic and cloud-native application environments, he added.
Additionally, the Aviatrix Kubernetes Firewall provides support for YAML files and open-source Terraform tools to make it simpler to include it within the context of a larger declarative DevSecOps workflow, noted Sengupta.
Responsibility for deploying firewalls today varies widely from one organization to another. In some cases, the cybersecurity team is responsible for all operations. In other instances, responsibility for security operations is being shifted over to DevOps and IT operations teams as part of an effort to apply more resources to discovering potential threats before the organization is impacted. Achieving that goal, however, requires making it simpler to manage cybersecurity tools and platforms within the context of workflows those teams are already employing to manage the rest of the IT environment.
Regardless of approach, securing cloud-native application environments is fundamentally different than a static on-premises IT environment used to deploy monolithic applications that are not usually updated nearly as frequently. Cybersecurity teams need to develop additional levels of expertise, because many of the legacy tools and processes they previously relied on are simply no longer applicable.
The challenge, as always, is that as the attack surfaces within an enterprise IT environment continue to expand, so does the number of opportunities for cybercriminals to take advantage of a mistake.