Uptycs Deepens CNAPP Support for Kubernetes
Uptycs today at the Kubecon + CloudNativeCon conference today added the ability to detect and highlight Kubernetes security issues and misconfigurations using the Goat playground to its cloud-native application protection platform (CNAPP) along with an ability to automatically apply security controls across the entire software development life cycle (SDLC).
Abhinav Mishra, director of product for Uptycs, said the ability to apply fine-grained image policies to detect vulnerabilities, malware and misplaced secrets is part of an ongoing effort to make it simpler to implement DevSecOps best practices.
Kubernetes Goat extends those capabilities using a framework for detecting cybersecurity issues that is now integrated with the Uptycs Sensor, which can now detect issues such as container breakouts, privilege escapes and role-based access control (RBAC) misconfigurations.
Customizable image policy controls also make it possible to identify and prioritize risk based on indicators of compromise (IoCs) or mark images as non-compliant if key requirements are not met. It then becomes possible to automatically remove sensitive data, malware and other exploitable vulnerabilities.
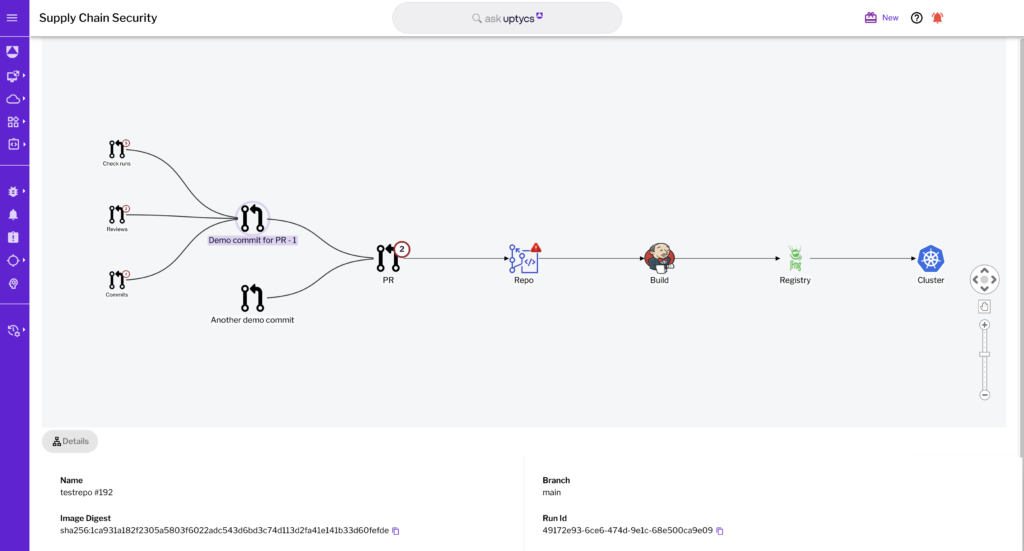
In addition, DevSecOps teams can leverage the Uptycs data lake embedded within its CNAPP to trace images from GitHub pull requests all the way to the Kubernetes runtime, where they are deployed from a single console.
Uptycs has been making a case for a CNAPP that includes extended detection and response (XDR) capabilities that can be used to secure endpoints. It analyzes data collected from platforms such as GitHub repositories, Microsoft Azure Active Directory (AD) and the Okta authentication platform.
Many cybersecurity teams are already using the Uptycs CNAPP to track and analyze malicious activity and centralize the management of cybersecurity. Instead of requiring security operations teams to stitch together multiple point products to address those concerns, the Uptycs approach provides a unified platform that aims to reduce the total cost of cybersecurity.
A lot of progress has been made in terms of adopting DevSecOps, but it’s still early days. The goal should be to reduce the cognitive cybersecurity load on developers to the point where they can focus more time on writing secure code. That requires adopting tools and platforms to secure the software supply chain that doesn’t materially slow down the rate at which applications are built and deployed. That’s a major challenge because the applications being developed today are considerably more complicated than legacy monolithic applications. On the plus side, however, they are easier to update whenever an issue is discovered because the container used to construct cloud-native applications can be more easily ripped and replaced.
It’s not clear how much cybersecurity teams are participating directly within DevOps workflows. Most developers, however, don’t have a lot of cybersecurity expertise, so asking them to secure application development tools and platforms on their own is not likely to have as big an impact as organizations might hope. The challenge and the opportunity now is to find a way to automate DevSecOps processes as much as possible.