Sysdig Dives Deeper into AWS Container Security
Sysdig announced today it has extended its alliance with Amazon Web Services (AWS) to provide automated inline image scanning for AWS Fargate containers via the Amazon Elastic Container Registry (ECR). Sysdig claims this is the first inline container scanning tool for Fargate, which is an event-driven platform through which AWS automatically makes infrastructure available to container applications as they scale.
In addition, Sysdig announced its open source Falco threat detection platform has been integrated with AWS CloudTrail, the logging tool AWS makes available to IT teams that need to troubleshoot cloud deployments. Logs created by AWS CloudTrail now can be automatically ingested into Falco to detect threats across containers, hosts, Kubernetes and AWS services via a unified interface. The Falco engine is an incubating project now being developed under the auspices of the Cloud Native Computing Foundation (CNCF). Sysdig, however, provides its own commercial interface for Falco.
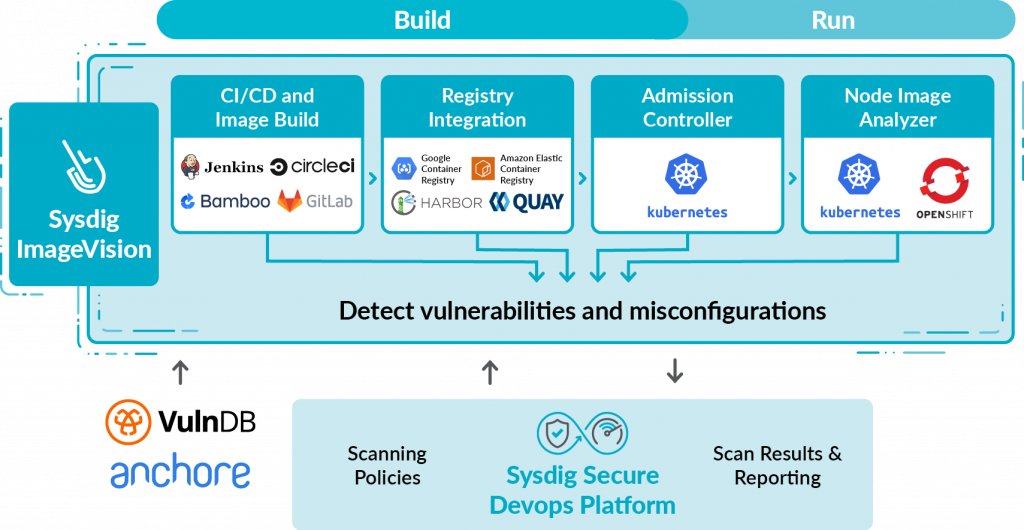
The capabilities are being made available via the Sysdig Secure DevOps Platform, a software-as-a-service (SaaS) platform. A ContainerVision module collects and correlates granular data from infrastructure, services and applications. Sysdig ServiceVision then contextualizes that data with Kubernetes and AWS service data. ImageVision then identifies and prevents images with vulnerabilities or misconfigurations from being shipped.
Pawan Shankar, director of product marketing for Sysdig, says the challenge Fargate presented was finding a way to scan inside the AWS environment without requiring image sharing and access to credentials outside of the registry. Solving that issue requires Sysdig to integrate its scanning tools within Amazon ECR to allow it to listen for when Fargate tasks are about to be launched, which then triggers an automated scan, he says.
Sysdig already provides support for other AWS services such as Amazon Elastic Container Service (ECS) and Amazon Elastic Kubernetes Service (EKS). Sysdig can, for example, show information about workloads running in Fargate and functions running in Lambda alongside container, Kubernetes and services metrics. Curated Prometheus exporters, dashboards templates and documentation for Fargate and Lambda are available on PromCat.io, an open source repository of Prometheus integrations maintained by Sysdig.
The goal is to make it easier for organizations that rely on AWS to run container applications to embrace best DevSecOps practices, says Shankar. Falco makes it possible to automatically detect unauthorized access to services, publicly exposed accounts and other anomalies in addition to being able to manage policy as code within the context of a DevSecOps practice, he notes, adding Sysdig bundles more than 100 rules with its implementation of Falco to make it simpler to implement those policies.
Fargate is positioned by AWS as a serverless framework in the context that IT teams never have to configure infrastructure resources on behalf of developers. AWS claims IT teams are running tens of millions of containers on Fargate each week.
It’s not clear to what degree IT teams ultimately will rely on managed services such as Fargate to automate the care and feeding of container applications. The one thing that is certain is that no matter what the platform, the chances developers may have unwittingly encapsulated vulnerabilities in their application remain fairly high.