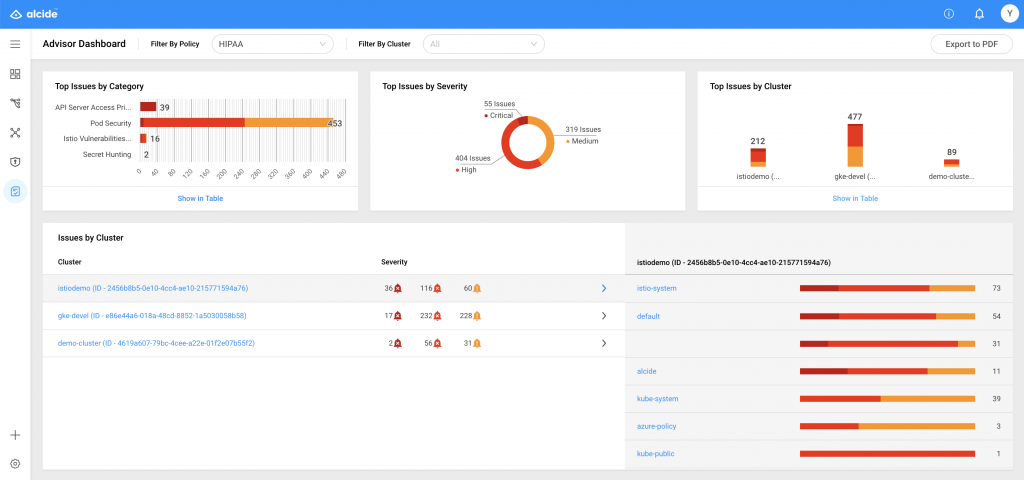
Alcide Adds HIPAA Support to Kubernetes Compliance Tool
Alcide today announced it is adding support for Healthcare Information Portability and Accountability (HIPAA) compliance to a scanning tool it provides for Kubernetes to organizations that need to comply with a variety of regulations.
In addition, Alcide is pledging to make the tool available for free to healthcare organizations for the duration of the COVID-19 pandemic.
Alcide CEO Amir Ofek says that while HIPAA compliance doesn’t mean healthcare organizations are secure, it does present a litmus test for assessing the cybersecurity posture of the organization. The free offer is being extended to not just healthcare facilities, but also research firms and healthcare insurance providers.
 Kubernetes has become a bigger attack vector, Ofek notes, because many cybercriminals are focused on cloud services that are relatively easy to penetrate because, for example, someone in IT misconfigured a port. Once inside that public cloud, many of the high-value targets cybercriminals are trying to compromise are modern applications running on Kubernetes clusters.
Kubernetes has become a bigger attack vector, Ofek notes, because many cybercriminals are focused on cloud services that are relatively easy to penetrate because, for example, someone in IT misconfigured a port. Once inside that public cloud, many of the high-value targets cybercriminals are trying to compromise are modern applications running on Kubernetes clusters.
More troubling still, because of the economic fallout caused by the COVID-19 pandemic it’s probable there will be more people globally who have IT skills and are out of work. Many of those individuals will be tempted to engage in cybercriminal activity to pay their bills, Ofek says. In fact, the volume of cybercriminal activity inspired by the COVID-19 pandemic is already on the rise.
Unfortunately, many organizations will not have the economic resources they previously relied on to thwart those attacks. As a result, Ofek says there will be more pressure to shift responsibility further left on to the shoulders of developers as part of what will soon be an accelerated transition toward implementing best DevSecOps processes.
Of course, compliance is only one aspect of the larger DevSecOps equation. In terms of compliance mandates, Alcide already supports within its auditing tools the General Data Protection Rule (GDPR) and the Payment Card Industry Data Security Standard (PCI DSS). Overall, however, the company has been making a case for programmatically addressing security and compliance requirements using a platform designed from the ground up to run natively on Kubernetes clusters. In contrast, rival platforms are focused mainly on trying to secure the containers that make up a microservice, he says.
It’s too early to say how the COVID-19 pandemic might impact Kubernetes adoption. On the one hand, there will be many organizations that won’t have the resources available to fund a transition to a modern IT environment anytime soon. On the other hand, many IT organizations will look to leverage containers to lift and shift even more applications into the cloud at a time when physical access to local data centers is limited. Once that shift occurs, those applications can then be modernized in phases using microservices based on containers. Most of those microservices will wind up running on a Kubernetes cluster in the cloud.
No matter what the path forward, however, whenever a Kubernetes cluster is employed someone within the IT organization will be needed to secure it. The only real question is whether that person will be a developer who has mastered cybersecurity or a member of the cybersecurity team that has the skills needed to write the required code.


