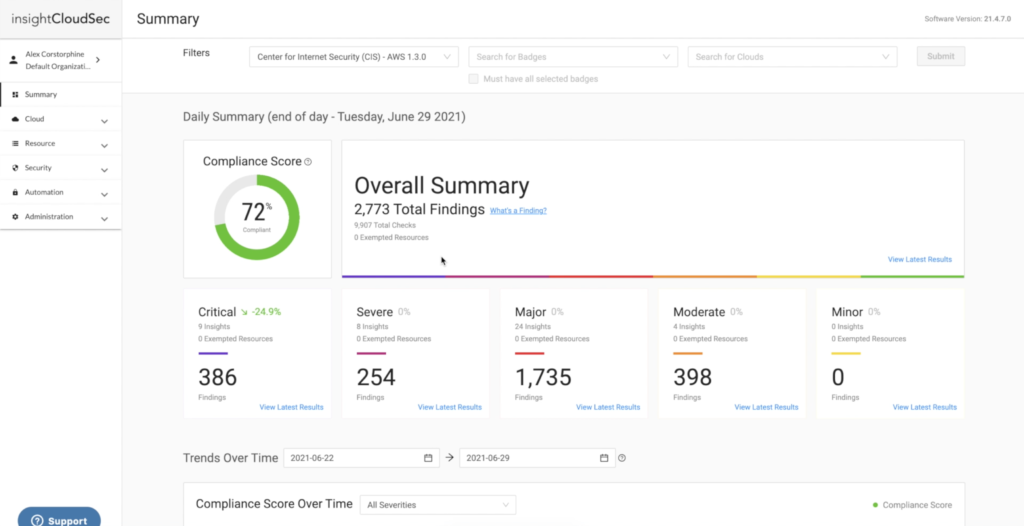
Rapid7 Unifies Alcide and DivvyCloud in Single Platform
Rapid7 this week launched an InsightCloudSec platform that combines the cloud security posture management (CSPM) platform it gained with the acquisition of DivvyCloud last year and the Kubernetes security platform it gained with the acquisition of Alcide earlier this year.
Brian Johnson, senior vice president for cloud security at Rapid7, says as cybersecurity becomes more complex and challenging to maintain organizations are looking to centralize the management of security platforms. This is part of an overall effort to enable security teams to become more efficient and also reduce the total cost of cybersecurity.
As part of that effort, the InsightCloudSec platform provides unified visibility and context across multi-cloud environments that enable cybersecurity teams to analyze, prioritize and remediate issues as they arise. There are also infrastructure-as-code (IaC) templates to identify risk early in the CI/CD pipeline and tools for automating workflows. Via the Rapid7 InsightCloudSec platform, cybersecurity teams will be able to secure everything from traditional virtual machines to containers and serverless computing frameworks, says Johnson.
Johnson says in the wake of a series of high-profile software supply chain compromises, it’s clear organizations are reevaluating their approach to application and infrastructure security. In an ideal world, organizations would be embracing DevSecOps best practices in a way that shifts more responsibility for security further left toward developers. In practice, many organizations are building and deploying applications at a pace that requires them to reconsider the business value derived from deploying applications faster only to discover a raft of security issues after they have been deployed in a production environment.
Organizations will need to strike a better balance between those two competing priorities by tightening the guardrails that should be in place because the risk is now much higher, notes Johnson.
In many cases, the developers themselves have been identified as the weakest link in the software supply chain. Unfortunately, many of those developers are just as likely to fall prey to a clever phishing attack as anyone else.
Of course, the challenge is that many organizations are now deploying more complex microservices-based applications in Kubernetes environments. The possibility that developers will misconfigure a Kubernetes cluster or discover a compromised individual application programming interface (API) that provides access to the rest of the application environment is high. In some cases, organizations may even decide to deploy a monolithic application as an alternative simply because they have greater confidence in their ability to secure it.
Johnson says most organizations will continue to build and deploy applications as fast as they can, but the speed at which that occurs today is likely to be impacted by reviews of the software supply chain. Developers are not going to acquire the expertise required to secure application environments overnight. However, it’s clear cybercriminals are now successfully compromising software supply chains that cybersecurity teams are being tasked with securing immediately.
In many ways, the focus on securing software supply chains is just another example of an IT pendulum swinging back from one extreme to another, says Johnson. Eventually, the hope is that the pendulum will settle at a point where DevOps teams can continue to build and deploy applications that are actually secure as fast as possible.