Chainguard Dashboard Provides Visibility into Pipeline for Creating Secure Container Images
Chainguard today added a dashboard that provides visibility into which software packages the provider of secure container images is currently prioritizing.
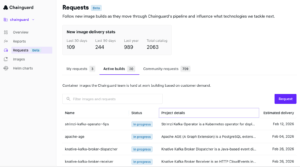
Ed Sawma, vice president of product marketing for Chainguard, said the Fulfillment Dashboard will improve planning by providing organizations with timelines for completing specific projects.
Chainguard is already providing access to more than 2,000 secure container images via a hub it manages. Which projects are prioritized, however, is heavily influenced by the number of requests made by individual customers, said Sawma. The Fulfillment Dashboard provides some insight into which projects are being prioritized by the internal Chainguard development team based on that feedback, he added.
That approach, hopefully, will reduce the number of duplicate requests being made in addition to eliminating the need to rely on email and Slack communications with the Chainguard customer success team members to check the status of any given project, he noted.
It’s not clear how many organizations have adopted secure container images, but as cyberattacks against software supply chains have increased, the need for them is becoming much more apparent. At the moment, Chainguard has more than 400 customers, but the number of organizations using container images to build application numbers in the tens of thousands.
Many organizations that adopted containers also have a false sense of security based on the fact that containers are typically ripped and replaced frequently. However, the software encapsulated in those containers often contains any number of vulnerabilities, many because one application developer or another downloaded an older version of a software component.
Arguably, the easiest vulnerability to remediate is the one that was never created in the first place. In fact, nothing slows the pace of application development and deployment down more than a vulnerability that is discovered just before an application is supposed to be deployed. As such, one of the ways that application developers can accelerate the pace of application development is to eliminate vulnerabilities before they are discovered in a software build, or worse yet, in a production environment.
After all, the one thing no application developer wants is to be called out for not fixing the one vulnerability that resulted in the organization having to choose between missing an application deployment deadline and deploying software that might enable one or more exploits to wreak all kinds of cybersecurity havoc. A combination of carelessness and pressure to meet application delivery deadlines is all too often the root cause of more application security incidents than most application development teams would care to admit.
Hopefully, in the age of AI the quality of the container images being created will improve. Unfortunately, in the short term AI coding tools are generating more vulnerabilities than ever, many of which then find their way into a production environment.
In the meantime, however, application development teams would be well advised to review the security of the container images running in their production environments because chances are high that many of them will be found to be wanting.