Octarine Adds 2 Open Source Projects to Secure Kubernetes
Octarine announced today it has launched two open source projects intended to enhance Kubernetes security.
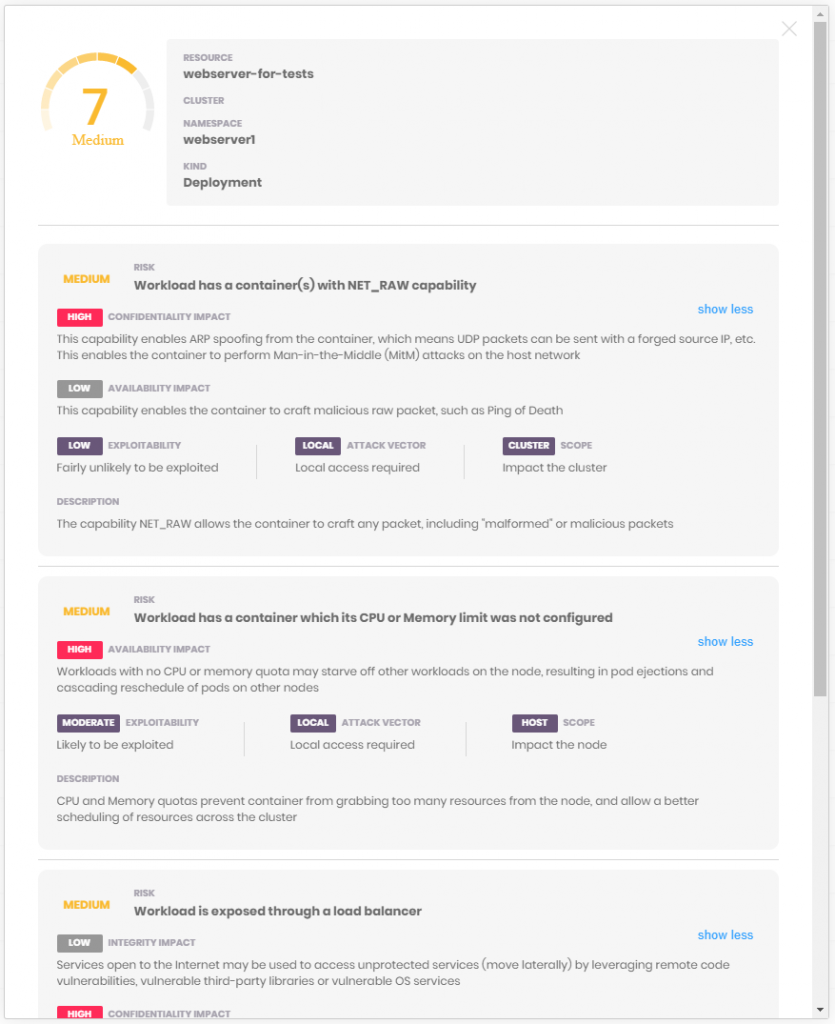
The first project is kube-scan, a workload and assessment tool that scans Kubernetes configurations and settings to identify and rank potential vulnerabilities in applications in minutes. The second project is a Kubernetes Common Configuration Scoring System (KCCSS), a framework for rating security risks involving misconfigurations.
Julian Sobrier, head of product for Octarine, said the projects are extensions of the namesake cybersecurity framework the company created based on a service mesh for Kubernetes clusters. The Octarine service mesh not only segments network and application traffic all the way up through Layer 7 running on Kubernetes clusters, but it also acts as an inspection engine that employs machine learning algorithms to identify anomalous traffic, Sobrier says.
Because the Octarine service mesh runs natively on Kubernetes, Octarine is also designed from the ground up to integrate via application programming interfaces (APIs) and command-line interfaces (CLIs) with continuous integration/continuous deployment (CI/CD) platforms to further adoption of best DevSecOps practices, he says.
Sobrier notes there are more than 30 security settings on a Kubernetes cluster, which makes it probable that any one of them is likely to be misconfigured on one or more clusters at some point. KCCSS and kube-scan employs compliance benchmarks defined by the Center for Internet Security (CIS) to identify misconfigurations for both Docker containers and versions 1.6 and 1.7 of Kubernetes. Both projects will provide support for future versions of Kubernetes as well, he says.
KCCSS is modeled on the Common Vulnerability Scoring System (CVSS) used to rate vulnerabilities. However, rather than focusing on vulnerabilities, it has been applied to configurations and security settings. KCCSS scores both risks and remediations as separate rules, which allows IT teams to calculate risk for every runtime setting and application workload.
kube-scan, based on KCCSS, is a free assessment tool that analyzes more than 30 security settings and configurations, including privilege levels, capabilities and Kubernetes policies, to establish a risk baseline. It identifies which workloads are most at risk and potential consequences, and helps prioritize remediation efforts via updates to Kubernetes Pod Security Policy, Pod definitions and manifest files. kube-scan runs as a pod but does not allow ingress or egress access, which makes it safe to run on any distribution of Kubernetes.
As Kubernetes adoption in production environments increases, it’s now only a matter of time before cybercriminals start routinely scanning for Kubernetes misconfigurations. With DevOps teams now assuming more responsibility for security, the most immediate challenge many organizations face is arming those teams with the tools needed to secure their environments. Many of the legacy cybersecurity tools organizations have in place simply don’t work for Kubernetes. DevOps teams, however, have also shown a strong preference for open source tools that are easily accessible. Those tools may not secure the entire Kubernetes environment, but they do at least provide a starting point on which organizations over time can build a more robust framework.