Trend Micro Details Attack Against Containers
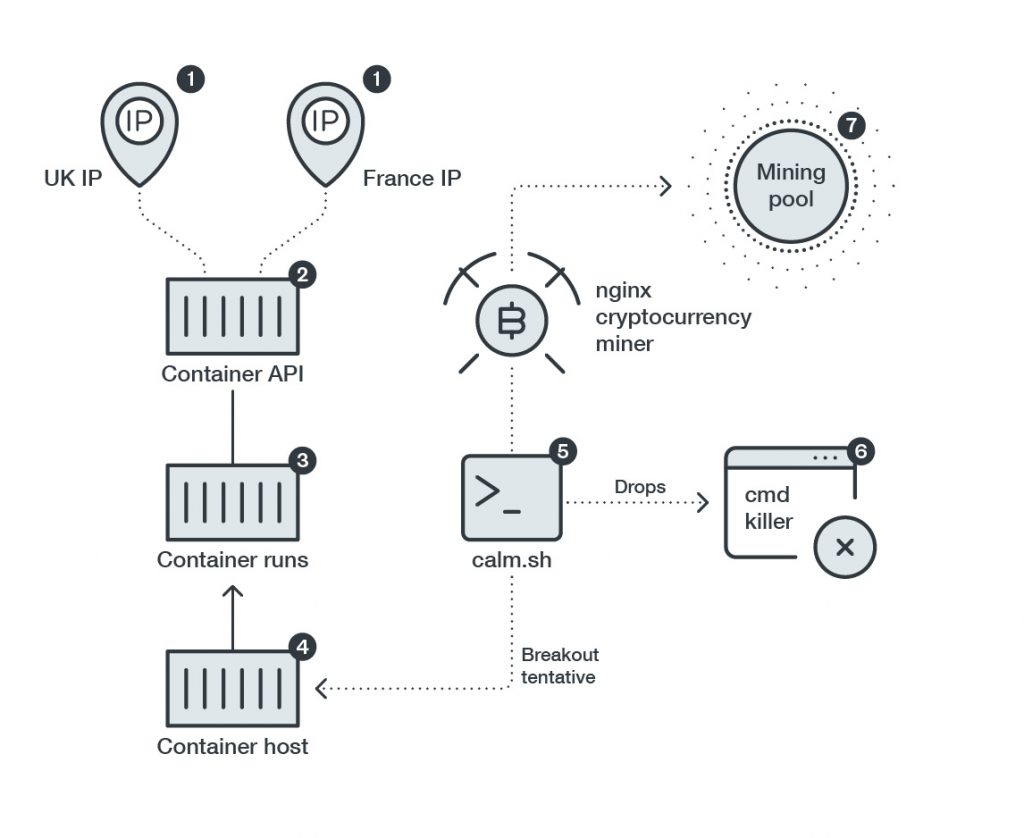
Trend Micro revealed this week it has encountered a malicious payload within a Docker container; the payload was specifically crafted to escape from a privileged container in a way that would enable malware to infect all the workloads running on a host machine.
Mark Nunnikhoven, vice president for cloud research for Trend Micro, says that while most Docker containers are not running in privileged mode, the attack shows cybercriminals are getting more adept at exploiting the loosely isolated nature of containers sharing the same host machine. The biggest issue is that, once a container is configured in a privileged mode, it is rarely turned off.
Most of the compromises involving Docker containers (at least those that have been disclosed) typically involve some form of crypto-jacking malware employed by cybercriminals to surreptitiously mine digital currency. Many IT professionals tend to view those breaches as the digital equivalent of a victimless crime, especially when the infrastructure being compromised belongs to a cloud service provider. However, Nunnikhoven says as attacks against containers become more sophisticated, it is clear cybercriminals are starting to realize that there is a correlation between containers and high-value application targets. Any organization that has the resources to build and deploy containerized application is likely driving a process involving, for example, a digital business transformation initiative that generates a large volume of sensitive data, Nunnikhoven says.
Too many developers assume that, because a container doesn’t tend to run for very long, there is little chance of it being compromised. In reality, cybercriminals have developed automation capabilities that enable them to compromise an entire software supply chain, and the platforms it depends on, in a matter of minutes, says Nunnikhoven.
On the plus side, cybersecurity defenses are also becoming more automated. Not only is it becoming easier to apply cybersecurity policies using Kubernetes application programming interfaces (APIs), Nunnikhoven says automation frameworks provided on top of those APIs by vendors, such as Trend Micro, are making it possible to both detect threats faster and remediate vulnerabilities across an extended software supply chain. In effect, an automation arms race between cybercriminals and cybersecurity vendors is now well underway, Nunnikhoven says. Cybersecurity teams should expect to see more behavioral analytics technology that can identify anomalous container behavior indicative of malware, says Nunnikhoven.
In the meantime, application security needs to go well beyond simply scanning containers for vulnerabilities, Nunnikhoven adds. In the wake of some recent, high-profile security breaches involving software supply chains, it is clear cybersecurity teams will be paying more attention to how software is constructed. That may eventually lead to greater adoption of DevSecOps best practices.
In the shorter term, however, teams may also uncover application development processes that take for granted the inherent security of a container downloaded from a repository. Organizations should have their own container repositories through which all the code that is incorporated into a software supply chain is regularly vetted.
Unfortunately, it’s now more a question of how and when containerized applications will be breached, rather than if. Hopefully, the damage inflicted will remain relatively minor, but most cybersecurity professionals probably wouldn’t take bets on it.