Why Secure-by-Design CI/CD Matters in Cloud-Native Systems
CI/CD pipelines are a core part of modern cloud-native systems. They help teams build, test and deploy software quickly. In the past, CI/CD was mainly about automation and speed. Today, it is also about security, reliability and governance.
In enterprise and regulated environments, CI/CD pipelines must be secure by default. If security is added late, it can slow teams down and increase risk. This article explains why secure-by-design CI/CD is important and how it helps cloud-native systems scale safely.
The Hidden Risks in Cloud-Native CI/CD
Cloud-native platforms give teams flexibility, but they also introduce new risks when pipelines are not designed properly. Common challenges include:
- Using unapproved or inconsistent base images
- Missing security scans during builds
- Storing secrets directly in pipeline files
- Differences between development and production environments
- Limited audit logs for pipeline changes
These issues may look small; however, at scale, they can cause serious security and operational problems.
What Secure-by-Design Means in CI/CD
Secure-by-design CI/CD means that security is built into pipelines from the start. It does not mean slowing developers down or adding manual approvals everywhere.
In practice, secure-by-design CI/CD includes:
- Standard pipeline templates with baseline security controls
- Approved base images and controlled artifact repositories
- Automated vulnerability scanning during builds
- Secure secrets management instead of hard-coded credentials
- Clear separation between build and deployment stages
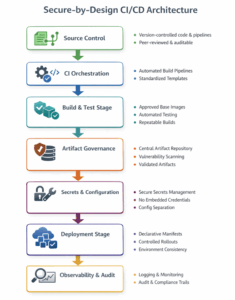
Secure-by-Design CI/CD Architecture
A typical cloud-native CI/CD flow in an enterprise environment looks like the following:
High-Level CI/CD Flow
1. Source Control
-
- Application code and pipeline definitions are version controlled.
- Changes are peer-reviewed and auditable.
2. CI Orchestration
-
- Build pipelines are triggered automatically on code changes.
- Pipelines follow standardized templates maintained by platform teams.
3. Build and Test Stage
-
- Applications are built using approved base images.
- Automated tests run early to detect functional issues.
- Container images are produced in a repeatable manner.
4. Artifact Governance
-
- Built artifacts are stored in a central, governed repository.
- Images are scanned for vulnerabilities before promotion.
- Only validated artifacts are eligible for deployment.
5. Secrets and Configuration Management
-
- Secrets are injected securely at runtime.
- No credentials are embedded directly in pipeline definitions.
- Configuration is separated from application code.
6. Deployment Stage
-
- Deployments are performed using declarative manifests.
- Environment-specific values are managed consistently.
- Rollouts are observable and reversible.
7. Observability and Audit
-
- Pipeline executions, deployments and changes are logged.
- Monitoring and alerting provide visibility into runtime behavior.
- Audit trails support compliance and incident investigations.
Why This Architecture Matters
This architecture ensures that:
- Security controls are enforced automatically, not manually.
- Developers interact with secure defaults rather than custom pipelines.
- Platform teams can evolve controls centrally without disrupting delivery.
- CI/CD remains fast, predictable and auditable at scale.
Most importantly, it treats CI/CD as a platform capability, not a collection of ad hoc scripts.
Balancing Developer Speed and Governance
Security and speed are often seen as opposites, but they do not need to be. When pipelines provide secure defaults, developers spend less time fixing security issues later.
Platform and DevSecOps teams help by:
- Providing shared pipeline templates
- Reducing repeated security work across teams
- Making secure practices easy to follow
Lessons From CI/CD at Scale
At scale, small pipeline mistakes can affect many teams. Secure-by-design pipelines help reduce this risk by creating consistency.
Key lessons include:
- Consistency is more important than tool choice.
- Central standards reduce operational risk.
- Clear audit trails help during incidents and reviews.
The Future of CI/CD
CI/CD systems are becoming more intelligent. Future pipelines will help engineers understand risks and make better decisions.
Conclusion
Secure-by-design CI/CD is essential for cloud-native systems. It helps organizations move fast while keeping systems safe and reliable.