Why DockSec is the Security Layer Your Dockerfiles Were Missing
You used to scan containers with Trivy, then lint them using Hadolint. After that, you hoped your developers would review the output and take action. Alas, in fast-paced pipelines, hope doesn’t secure anything. DevSecOps today demands more than static alerts and silent failures. It needs smart tools that speak your language.
DockSec answers that call with precision and power. You use it like any open-source tool, but the results feel different. It doesn’t just flag issues, it explains every threat in simple language, which can be acted upon. You see rankings, not noise, real priorities you can fix now.
By blending artificial intelligence (AI) with trusted scanning methods, DockSec gives you what older tools miss. You understand each risk in context; you receive guidance; you move faster, solving problems without guesswork. In today’s DevSecOps world, that difference saves time and stops breaches.
This article walks you through how DockSec works, what makes it different and why it matters for modern DevSecOps workflows.
What is Broken With Traditional Docker Security
Static tools like Trivy, Hadolint and Docker Bench are essential for your container workflow. You rely on them to scan code, detect misconfigurations and catch vulnerabilities. But while these tools offer critical insights, they often create more questions than answers. Not only do you need detection, but you also need direction.
First, you face alert fatigue. These tools trigger endless warnings, but they don’t rank risks clearly. You are left sorting through dozens of findings without knowing what matters most. When every alert looks urgent, your team wastes time chasing the wrong problems. It slows delivery and adds confusion to your workflow.
Second, there is no built-in fix path. You get technical flags such as ‘use non-root user’ or ‘update base image’, but no readable instructions. You need to hunt for documentation or guess at solutions. That guesswork leads to delays or incorrect fixes. In fast pipelines, these gaps turn minor issues into security debt.
Third, the reports feel like they are made for machines. You see raw common vulnerabilities and exposures (CVE) codes, obscure output or long JavaScript object notation (JSON) dumps. Your developers need plain language, context and actionable steps. Without that, findings go ignored, even if they are serious.
Finally, the timing is off. Static tools often provide feedback too late — after a merge or during deployment. By then, you are already deep into production. Fixes become harder and costlier, and your team ends up patching instead of preventing. That’s not sustainable in a high-speed DevSecOps culture.
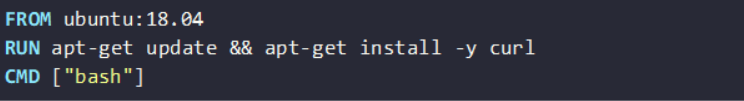
For example, here is a basic Dockerfile with security issues:
A traditional scanner might flag:
- Outdated base image (Ubuntu 18.04)
- No USER directive (runs as root)
- No checksum validation for package installs.
But it won’t tell you how to fix it, or which issue is most critical.
Why Does This Matter?
- 63% of container breaches stem from insecure images
- Most static scanners lack remediation context
- DockSec bridges the final mile from detection to action, with AI.
What DockSec Does Differently
DockSec fills the gaps your static tools leave behind. It doesn’t throw out Trivy, Hadolint or Docker Bench; it partners with them. You still scan your Dockerfiles, configs and containers the usual way. But instead of handing you raw logs or cryptic outputs, DockSec transforms that data into insights developers can use immediately. It connects technical depth with real-world understanding.
At its core, DockSec is powered by LangChain and large language models (LLMs), which means it doesn’t just report, it reasons. You get results that go beyond detection. Each issue is reviewed, contextualized and ranked by severity. DockSec analyzes what the problem means for your specific build or image, not just in theory. For example, if it finds a missing USER directive, it won’t just flag it; it will explain why running as root is dangerous and how attackers exploit it and will go ahead to give you a tested fix which you can apply directly.
This AI layer creates a developer-first experience. Instead of long CVE codes, you see short impactful summaries, threat scope and resolution steps. You also get risk scores, so you know what to fix first. The feedback is fast and embedded early in your continuous integration and continuous delivery (CI/CD) pipeline. You aren’t left chasing bugs after deployment. DockSec puts clarity and control back in your hands, making secure builds not just possible, but practical.
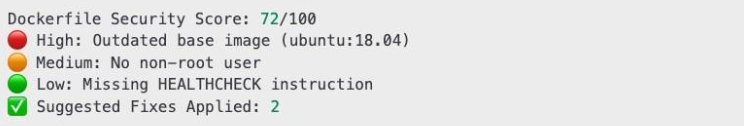
DockSec reads the Dockerfile, runs the scanners, feeds the output into a prompt chain and generates prioritized remediation: 
The AI output is then structured into a report like this:
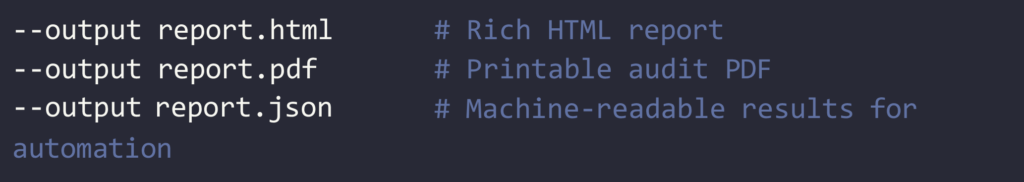
It also supports exports in multiple formats:
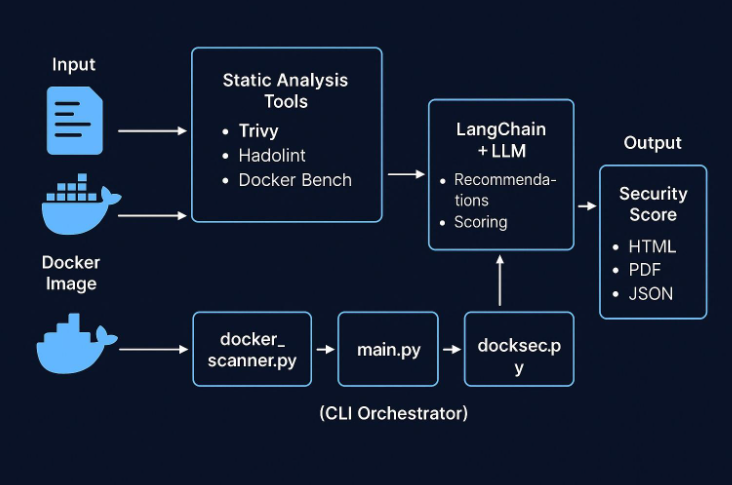
DockSec Architecture Overview
As shown above, DockSec operates in four stages:
- Input: Dockerfile or Docker image
- Static Analysis: Runs Trivy, Hadolint, Docker Bench
- AI Layer: LangChain + LLM to interpret findings
- Output: Reports in HTML, JSON, PDF, CLI
The command-line interface (CLI) makes it simple:
It also integrates easily into CI/CD pipelines:
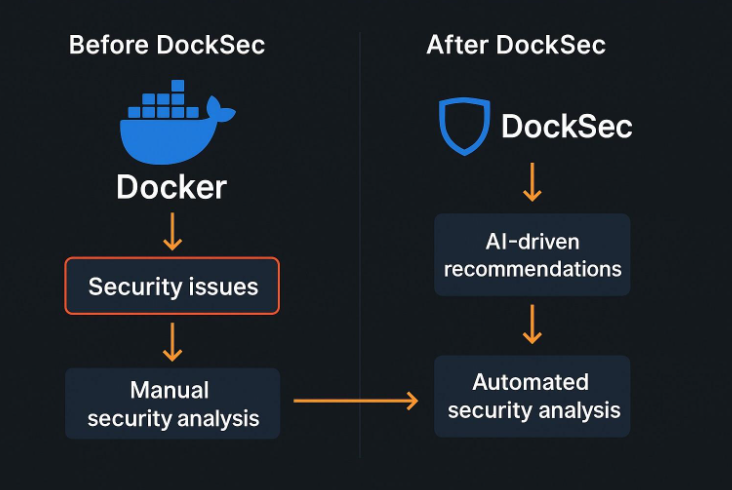
Before and After DockSec
Traditional tools stop at alerts. DockSec shows:
- Why it matters
- How to fix it
- What to fix first
This is especially useful in teams with:
- Developers who are new to Docker
You are still learning how containers work behind the scenes. Security best practices aren’t always obvious or well-documented. DockSec helps you avoid common mistakes like using the root user or outdated base images. It explains every risk in simple English, so you learn while you build.
- DevSecOps pipelines that have hard security gates
You work in a CI/CD pipeline with strict enforcement rules. If your build fails a security check, it doesn’t ship. DockSec prepares you with early, readable feedback. You fix issues before they block deployment and avoid last-minute surprises.
- Compliance workflows that demand audit-ready reports
Your team must comply with standards such as CIS, NIST or SOC 2 — which means clear documentation and proof of remediation steps. DockSec gives you structured, exportable reports with timestamps, descriptions and fix logs. You stay ready for audits without extra manual work.
Mini Case Study
A DevOps team at Dharam Digital, an online marketing service for content providers, integrated DockSec into their GitHub Actions pipeline. Within two weeks, their base image vulnerabilities dropped by 60%, and they automated remediation for 80% of flagged issues.
“We no longer guess what to fix — DockSec tells us,” says their co-founder, Krunal Doshi.
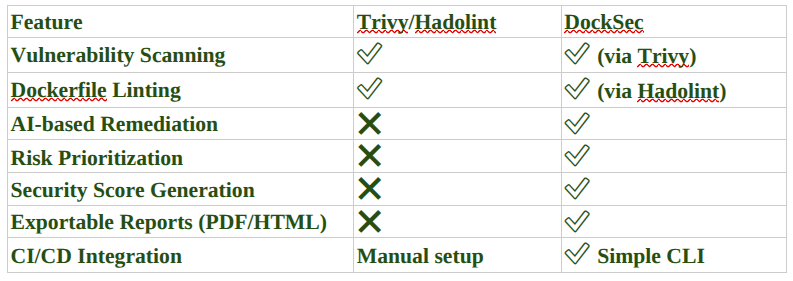
How DockSec Compares
Vision: Secure by Default, Developer First
DockSec is not just another scanner. It reflects a shift in mindset
- From detection to interpretation
- From alerts to action
- From security-as-a-blocker to security-as-a-guide
It also helps
- Developers understand and fix issues early
- Security teams enforce meaningful policy without noise
- Organizations demonstrate compliance with structured, exportable reports
The project is also being onboarded as an official OWASP project and has been accepted at multiple DevSecOps and research conferences, including the Open Cloud Security Conference and RSECon 2025.
Join the DockSec Community
DockSec is fully open-source and actively evolving:
- Run it locally: python3 docksec.py –dockerfile Dockerfile
–output report.html
- Contribute custom rules, test cases and language support
- Use it in your CI/CD and share feedback
Whether you are a security engineer, platform architect or an open source software (OSS) enthusiast, DockSec is built to help you ship secure containers without slowing down. It is helping redefine what intelligent DevSecOps tooling should look like.