Mastering Reloader: Automating Kubernetes Restarts with Confidence
In Kubernetes, managing configuration changes at runtime is an operational blind spot. Secrets get rotated, certificates expire and external systems update values your workloads depend on. Yet Kubernetes does not trigger automatic restarts when those changes occur. This is where Reloader becomes a game changer.
Reloader is the missing piece in your DevOps toolkit — bridging the gap between configuration changes and application readiness in real time.
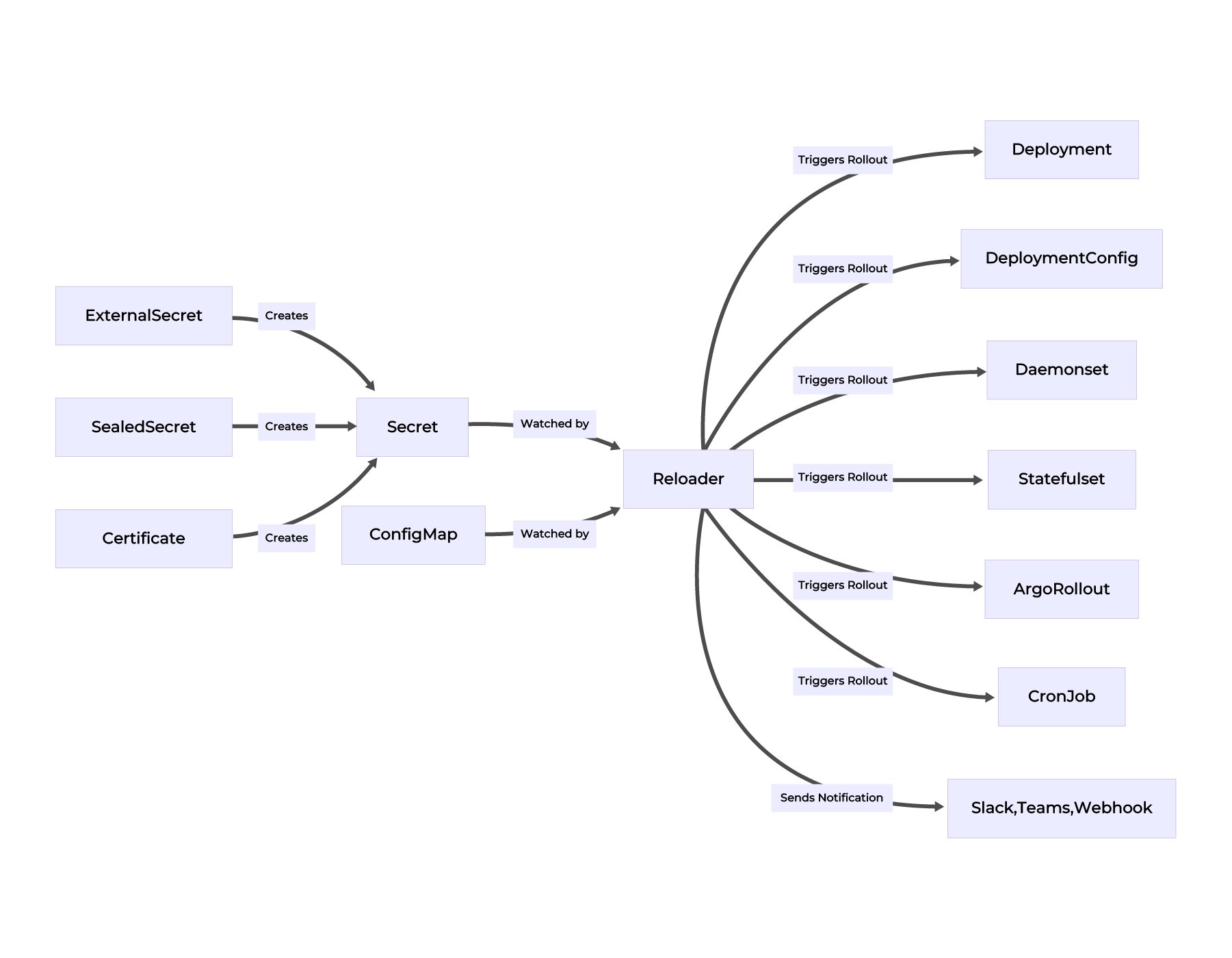
The diagram below summarizes how Reloader fits into a modern Kubernetes stack:
Let’s break it down and walk through everything Reloader does — from source to rollout.
What Reloader Watches
Reloader monitors Kubernetes resources that are commonly updated at runtime:
- Secrets, created or managed by:
- cert-manager (for TLS certificates)
- Manually created Secrets
- GitOps-managed Secrets
- ConfigMaps, which may be updated dynamically, manually or via automation pipelines.
No matter how the resource is delivered or updated, Reloader watches it live in the cluster.
What Reloader Does When Something Changes
When a Secret or ConfigMap is updated, Reloader triggers a Kubernetes-native restart for workloads that reference it. It works with:
- Deployment
- DeploymentConfig (OpenShift)
- DaemonSet
- StatefulSet
- ArgoRollout (progressive delivery)
- CronJob (job gets triggered again
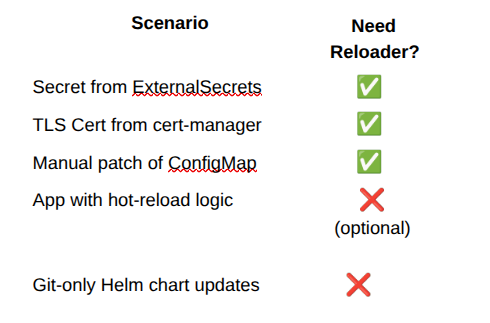
Use Cases Where Reloader Shines
1. Certificate Rotation (e.g., cert-manager)
When TLS certs renew automatically, most apps don’t detect the change unless restarted. Reloader bridges that gap.
2. Dynamic Secrets (e.g., External Secrets, Vault)
Secrets may be updated from external sources outside Git. Reloader ensures that workloads pick up the latest values.
3. Runtime Config Patching
Quick fixes to ConfigMaps or Secrets via kubectl? Reloader sees them and ensures that your app reloads cleanly.
4. GitOps + Runtime Harmony
Even in GitOps setups, Reloader protects against config drift caused by live changes not tracked in Git.
Notifications & Observability
Reloader Enterprise provides audit trails and alerting via:
- Slack
- Microsoft Teams
- Generic Webhook
Know exactly when and why something has restarted.
Why You Still Need Reloader in a GitOps World
Helm and ArgoCD rely on checksum annotations to detect config changes. But they only work when values change in Git.
What about real-time updates?
- Secrets issued via cert-manager
- Hot-patched ConfigMaps
- Dynamic values injected via External Secrets Git never sees those changes. Reloader does.
Real-World Feedback
“Reloader saved us hours of debugging config issues. Now our pods pick up secrets and certs automatically.” – Platform Engineer, FinTech start-up
“The cert-manager + Reloader combo is gold. Renewed certs, live and hassle-free.” – SRE, SaaS company
Getting Started With Reloader
Start with the OSS version:
kubectl apply -f https://raw.githubusercontent.com/stakater/Reloader/master/deployments/kubernetes/reloader.y aml
Reloader Enterprise is available for teams that want:
- Policy-based rollouts
- Audit logs
- Notifications
- A full control plane via console and API
Summary: Why Reloader Matters
Final Thoughts
If your workloads depend on configurations that can change dynamically, Reloader should be standard in your stack. It ensures that your applications are always aligned with your live cluster state — without hacks, scripts or surprises.