How AI and Python Can Transform Docker Security and Vulnerability Management
Portability and scalability have made Docker containers popular for application deployment, but security is a critical concern since gaps in container images can put whole systems at risk. Cybersecurity threats take advantage of outdated software, misconfigured systems and weak access controls to illegitimately infiltrate systems.
Using automated security scanning ensures that gaps are identified and addressed prior to deployment. To efficiently conduct security audits, Python offers efficient solutions, specifically using Trivy, Clair and Dockle.
In this article, we will explore how to build a Python-based vulnerability scanner, automating security audits and embedding scans into CI/CD pipelines to improve DevSecOps processes.
Setting Up the Vulnerability Scanner
Using Python to Interact with Docker Images
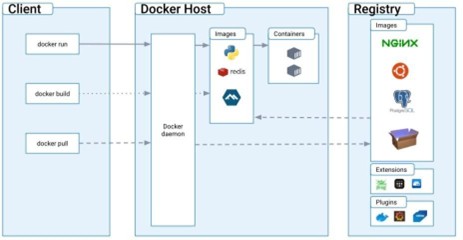
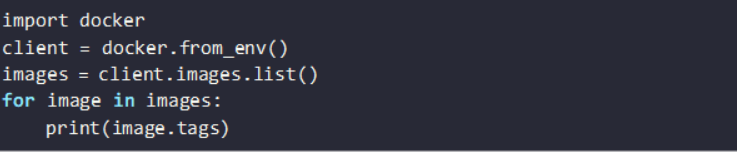
Python provides the docker-py software development kit (SDK), allowing developers to interact with Docker images and containers programmatically. With this library, you can enumerate existing images, fetch new ones and perform vulnerability assessments.
Install docker-py with:
Example code to list available images:
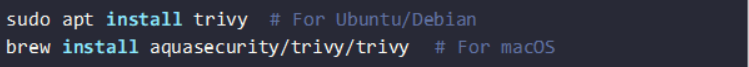
Installing and Integrating Trivy for Scanning Vulnerabilities
Trivy is a lightweight, open-source vulnerability scanner. Generally, it checks container images for known security flaws. To install Trivy, use:
To run a basic scan, use:
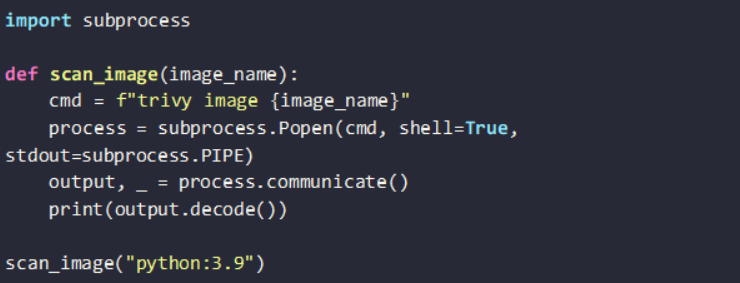
Scanning Images in Local and Remote Registries
Security scans must encompass both local container images and those stored in remote repositories such as Docker Hub, AWS elastic container registry (ECR) and Google container registry (GCR). The Python script below demonstrates how to use Trivy on a specified image:
Automating Security Audits with Python
Writing a Python Script to Scan for Vulnerabilities
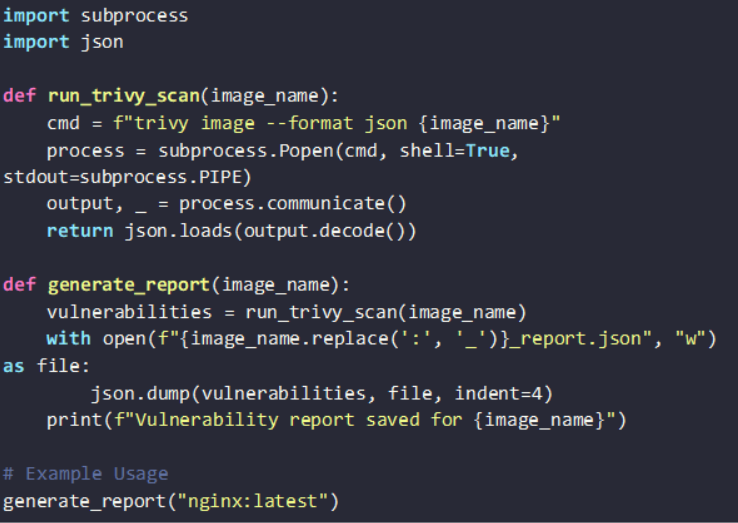
Automation reduces manual effort while ensuring continuous protection. The script below pulls images, runs security checks and generates reports:
Implementing JSON-Based Vulnerability Reports
Security reports should be structured for easy analysis. JSON format facilitates integration with monitoring tools and dashboards.
Scheduling Periodic Scans Using Cron Jobs & Airflow
Security scanning should be an ongoing process, so leverage tools such as cron jobs and Apache Airflow for scheduled scans.
Using Cron Jobs Schedule daily scans:
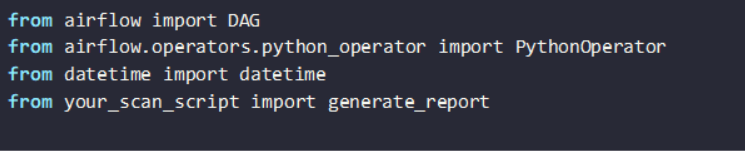
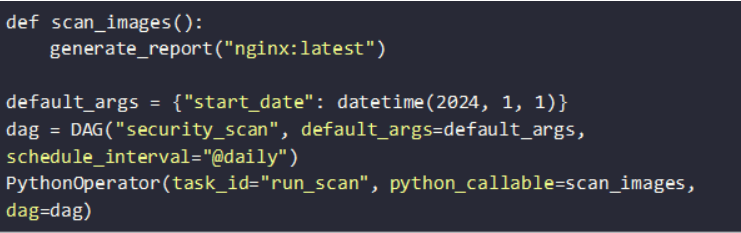
Using Apache Airflow
Airflow allows advanced scheduling and alerting. Define a directed acyclic graph (DAG) to scan images:
Enhancing the Scanner with CI/CD Integration
Integrating the vulnerability scanner with CI/CD pipelines enables security checks to happen automatically before deployment. It helps catch vulnerabilities early in the development cycle. Besides, it prevents insecure images from reaching production.
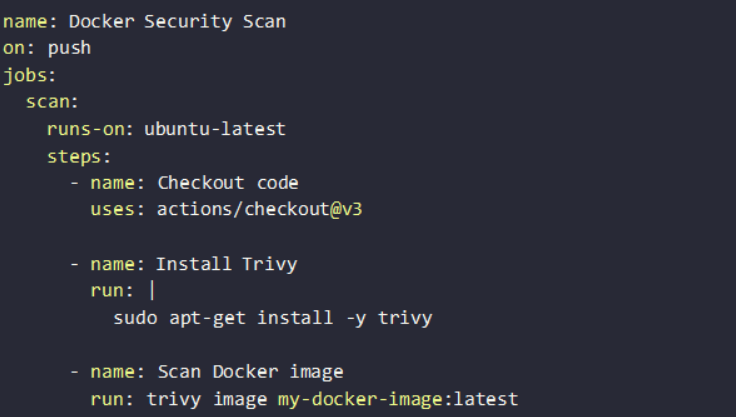
- Automating Scans in GitHub Actions & GitLab CI/CD
With GitHub Actions, you can automatically trigger a security scan whenever a new Docker image is built. Below is an example workflow using Trivy:
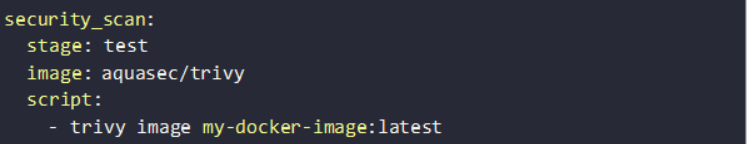
For GitLab CI/CD, a similar configuration can be added to .gitlab-ci.yml:
If vulnerabilities are found, the pipeline fails, stopping insecure images from being deployed.
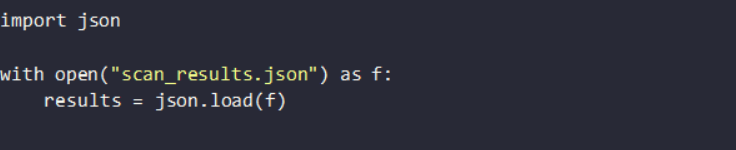
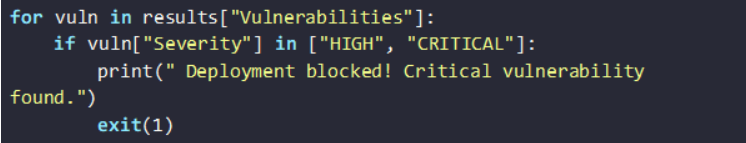
2. Blocking Deployment of Vulnerable Images
To enforce security, you can set up policy-based blocking. A Python script can analyze scan results and reject images with high-severity common vulnerabilities and exposures (CVEs):
The above script can be integrated into the pipeline as it will allow only safe images to proceed.
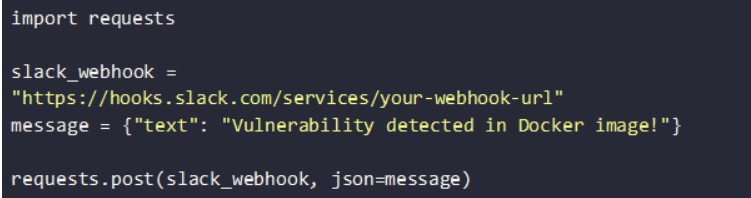
3. Sending Alerts via Slack & Email
You can use Slack webhooks and email alerts to notify security teams of issues. A Python script can send an instant notification when a security threat is detected:
This allows you to respond quickly to security threats.
Building an AI-Based Threat Detection Model
To make artificial intelligence (AI)-based threat detection models work, you need a machine learning (ML) model that can spot unusual activity inside Docker containers. Here’s how it’s done:
1. Choosing the Right Python Libraries
With Python, ML is streamlined owing to its extensive libraries. For a specific case of threat detection, you may use:
- TensorFlow or PyTorch: For creating deep learning models.
- Scikit-Learn: For less complex methods of anomaly detection like Isolation Forest or SVM.
- Pandas and NumPy: For data cleansing and organizing.
- Docker SDK for Python: To communicate with the containers and obtain the logs.
2. Collecting Data from Running Containers
To implement AI-enabled threat detection, it is critical to have access to considerable data, including logs and runtime information stored in Docker containers, such as:
- Process Activity: What processes are being executed inside the container?
- Network Traffic: Are there any unanticipated outbound connections being made from the container?
- CPU and Memory Consumption: Major increases may suggest hostile actions.
Pythonʼs Docker SDK lets you fetch these details easily:
The above command gives you raw data, but AI needs structured features. You must process the logs, extract key patterns and store them in a dataset for training your model.
3. Training the AI Model
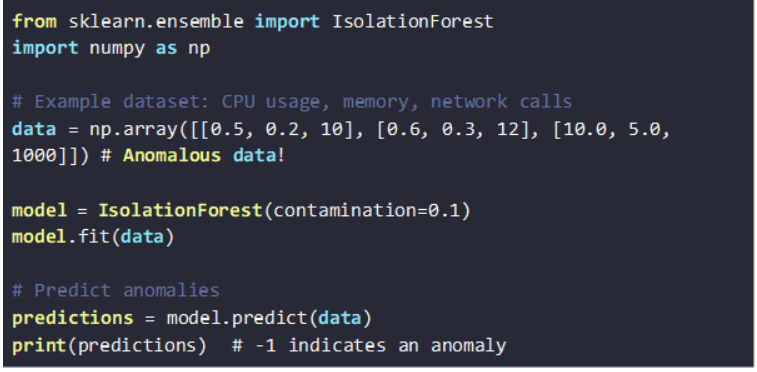
Now, feed the collected data into an ML model for threat detection. A simple approach is to use anomaly detection, where the model is trained on ‘normal’ container behavior and configured to flag anything unusual.
Using Scikit-learnʼs Isolation Forest algorithm for anomaly detection:
If the model flags a process as suspicious, log it and trigger alerts.
Deploying AI Models in Real-Time Security Monitoring
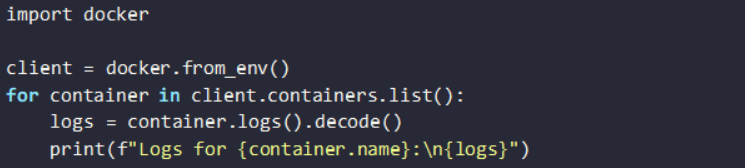
1. Integrating AI with Docker Logs
Continuous tracking of container activity is crucial for your newly developed AI model. Here’s what you can do:
- Code a program in Python that fetches logs in real-time.
- Review the logs to check for anomalous activities and errors.
- Deploy AI to automatically label the events as benign or malicious.
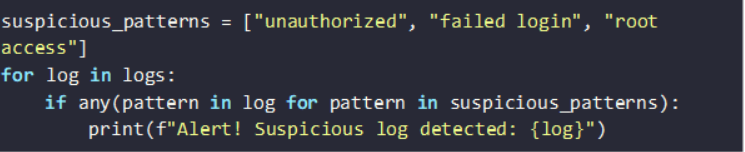
Example: Monitoring logs for unauthorized access attempts:
2. Detecting Zero-Day Attacks
AI is pre-eminent at spotting zero-day threats (new attacks that are not in security databases).
- If a container suddenly starts scanning the network, it is considered suspicious.
- If it downloads and runs an unknown script, it is a red flag.
Instead of relying on predefined rules, AI learns normal behavior and detects anything that deviates from it.
Final Thoughts
To conclude, integrating Python into the Docker security scanning process improves DevSecOps practices by automating vulnerability detection. With tools like Trivy, Clair and Dockle, developers can incorporate security into the development pipelines with ease.
In addition, emerging technologies are embracing automation powered by AI-driven threat detection and removal. To reduce cybernetic issues, containerized applications should be thoroughly scanned for vulnerabilities. This shift demands a fundamental change in developers’ mindsets.
Key Takeaways
- Docker images, if not properly scanned, can encompass several vulnerabilities that attackers may exploit.
- Python eases the automation of continuous security posture monitoring for container images.
- Trivy, Clair and Dockle are examples of tools capable of identifying security issues within Docker images.
- Integrating automated vulnerability scans into continuous integration and continuous development (CI/CD) pipelines helps prevent unsafe deployments.
- Automated alerts and reports enhance both security response and visibility.