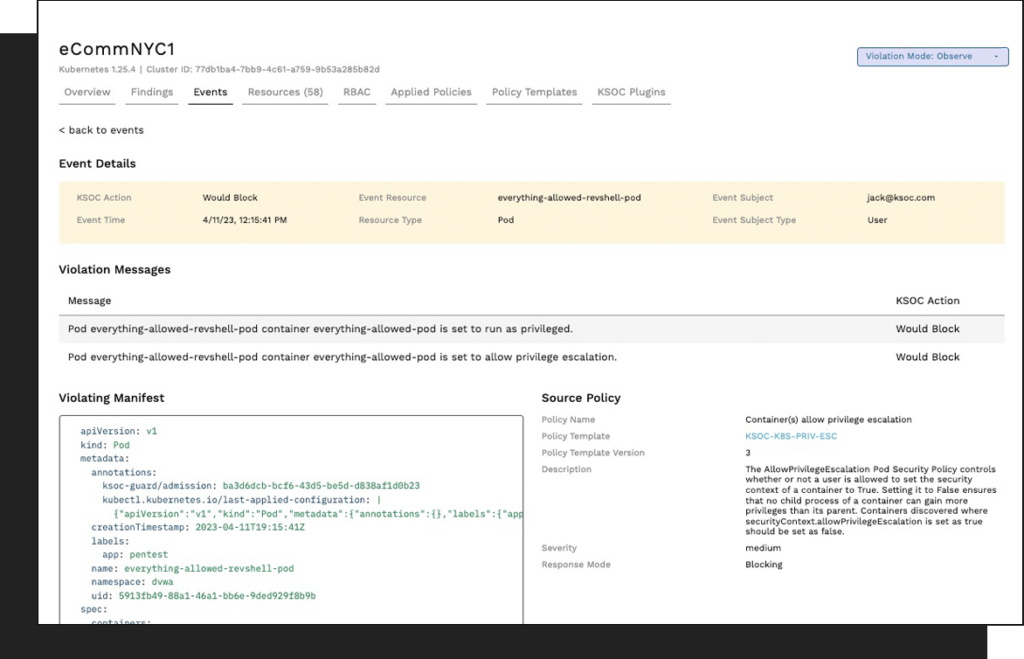
KSOC Unveils Security Posture Management Platform for Kubernetes
Kubernetes Security Operations Center (KSOC) has launched a security posture management platform that surfaces current and historical cyberattack activity in addition to providing remediation guidance.
Jimmy Mesta, KSOC CTO, said that real-time context is critical for securing ephemeral cloud-native application environments that are subject to frequent changes and updates. Other approaches to Kubernetes security posture management (KSPM) rely on polling intervals in an environment where containers may only be running for five minutes or less, he noted.
In contrast, the KSOC platform provides event-based misconfiguration alerts that can be sorted by source, said Mesta. Every event is instrumented in real-time, he added.
In addition, the platform will scan for vulnerabilities and generate software bills of materials (SBOMs), prevent workloads that don’t comply with defined policies from being deployed and aggregate and visualize what permissions have been granted to make managing role-based access controls (RBAC) simpler. That latter issue is especially challenging in Kubernetes environments, noted Mesta.
It’s not clear at what rate cyberattacks are being launched against Kubernetes clusters, but as more cloud-native workloads are deployed in production environments, it’s only a matter of time before cybercriminals target them. Many of these applications are driving digital business transformation initiatives that have become mission-critical for organizations, so any disruption might have a major adverse impact on revenue.
It’s already been demonstrated that cybercriminals have gained access to Kubernetes environments to mine for cryptocurrency. Most organizations should assume that, to one degree or another, their Kubernetes environment has already been compromised.
The challenge, of course, is that most Kubernetes environments are managed by DevOps teams that are still in the early stages of adopting DevSecOps best practices, and the number of cybersecurity professionals that understand how Kubernetes functions is extremely limited. As such, organizations will require a Kubernetes cybersecurity platform designed to be installed as a plugin that makes it simpler for the same team that manages a cluster to also manage cybersecurity, noted Mesta.
The issue is finding a way to apply guardrails at scale in a way that doesn’t slow down the pace of cloud-native application development, he added. Today, however, too many organizations are building applications at a pace that is unsafe because there are no cybersecurity guardrails in place, noted Mesta.
There is no doubt these issues will come back to haunt many organizations deploying those applications. There will soon be additional regulations holding organizations liable for application security. Attempting to apply policies and guardrails to an application after it has been deployed is infinitely more difficult than before, so it’s in the best interest of organizations to resolve Kubernetes security issues today.
In the meantime, it’s clear that cybersecurity is, once again, an afterthought as IT teams begin to adopt new cloud-native platforms for building and deploying applications. The issue now is now is finding a way to close that gap faster than when previous similar transitions to new platforms occurred.